Select the green color, which is specified at the corner of the pictures, and press the Shift key. This key is used to make rotate the picture on full speed and for each rotation it rotate for 15 degree.
Recent Comments
Tuesday, September 30, 2008
 9:51 PM
9:51 PM
 File Under :
Informative
File Under :
Informative
While working on word have you need to make pictures should be get rotated in between text. To do this, have you spending more time? If you want that the picture should be get rotate as slowly means you have to follow the actions as below.
Select the green color, which is specified at the corner of the pictures, and press the Shift key. This key is used to make rotate the picture on full speed and for each rotation it rotate for 15 degree.
Select the green color, which is specified at the corner of the pictures, and press the Shift key. This key is used to make rotate the picture on full speed and for each rotation it rotate for 15 degree.
 9:50 PM
9:50 PM
 File Under :
Informative
File Under :
Informative
The use of emails has become very much essential in personal and business life. Email has become more important than the phone or address of a person. When two people meet for the first time it is very common to exchange their email addresses for communication next time.
Daily we receive many different types of emails. Advertisements about products, emails requesting help, emails from adult websites, emails claiming that you have won a lottery or a prize, Or even emails from some country that they want to deposit a huge amount of money to your bank account etc. etc.
These Junk mails, Unsolicited mails or Spam emails we receive daily. It becomes a difficult task to identify them and deleted them manually.
To identify and delete SPAM mails there are many Spam filters available. Just like the Antivirus which identifies viruses and deletes them, Spam filters are used to identify and delete spam mails in your inbox.
Users of web based emails such as 'hotmail, yahoo or gmail' do not have to worry too much about SPAM, because these email servers use Spam filters to filter these unwanted emails from your inbox. However some spam mails somehow find their way into your inbox.
So whether you are using web mails or POP3 or IMAP mails, in addition to the SPAM filters at the server you also need to have a spam filter in your desktop computer. Only then you can effectively fight against SPAM.
Which is the best SPAM filter software? Mail Washer is one of the most popular spam filter software. Mail Washer can be used in Windows 95/98/NT/2000/XP. You can download Mail Washer at www.webwasher.com. Mail Washer is also available free. You can also buy Mail Washer. The paid Mai Washer has the following additional features.
* Support for IMAP servers.
* Supports Hotmail, MSN and AOL emails
* Enhanced, intelligent filtering is available
* Technical support is available.
* If you download the free software you can only use it for thirty days.
How does Mail Washer work?
Mail washer is used to filter SPAM mails and delete from your email inbox.
Just like your email client, Mail Washer also connects to the Mail server. It will identify the SPAM emails and list it. It can also delete the SPAM emails at the server itself without downloading it to your computer.
Mail Washer can also return the SPAM mails back to the sender. By doing this it creates an impression that your email address is wrong and thats why the mail has been returned. This will make the sender believe that your email is an invalid email and hence prevent further spam mails from the same sender.
Mail Washer also helps to create black lists and white lists. You can configure Mail Washer to delete black listed emails at the server and only download the white listed emails to your computer.
Which is better? Delete in the server? or Delete in the computer?
What will you do if you don't have the Mail Washer? you will download all mails including SPAM to your computer. So you are wasting your internet time and bandwidth. You also waste time by opening these spam mails and deleting them manually. Some spam emails also have 'web bugs' that can spy on you and send your secrets to the web bugs creator.
Using Mail Washer you can identify SPAM mails at the server and delete it there itself. Web bugs will not function. Only good emails will be downloaded to your computer. So you save on your internet time, bandwidth and your time and money.
Daily we receive many different types of emails. Advertisements about products, emails requesting help, emails from adult websites, emails claiming that you have won a lottery or a prize, Or even emails from some country that they want to deposit a huge amount of money to your bank account etc. etc.
These Junk mails, Unsolicited mails or Spam emails we receive daily. It becomes a difficult task to identify them and deleted them manually.
To identify and delete SPAM mails there are many Spam filters available. Just like the Antivirus which identifies viruses and deletes them, Spam filters are used to identify and delete spam mails in your inbox.
Users of web based emails such as 'hotmail, yahoo or gmail' do not have to worry too much about SPAM, because these email servers use Spam filters to filter these unwanted emails from your inbox. However some spam mails somehow find their way into your inbox.
So whether you are using web mails or POP3 or IMAP mails, in addition to the SPAM filters at the server you also need to have a spam filter in your desktop computer. Only then you can effectively fight against SPAM.
Which is the best SPAM filter software? Mail Washer is one of the most popular spam filter software. Mail Washer can be used in Windows 95/98/NT/2000/XP. You can download Mail Washer at www.webwasher.com. Mail Washer is also available free. You can also buy Mail Washer. The paid Mai Washer has the following additional features.
* Support for IMAP servers.
* Supports Hotmail, MSN and AOL emails
* Enhanced, intelligent filtering is available
* Technical support is available.
* If you download the free software you can only use it for thirty days.
How does Mail Washer work?
Mail washer is used to filter SPAM mails and delete from your email inbox.
Just like your email client, Mail Washer also connects to the Mail server. It will identify the SPAM emails and list it. It can also delete the SPAM emails at the server itself without downloading it to your computer.
Mail Washer can also return the SPAM mails back to the sender. By doing this it creates an impression that your email address is wrong and thats why the mail has been returned. This will make the sender believe that your email is an invalid email and hence prevent further spam mails from the same sender.
Mail Washer also helps to create black lists and white lists. You can configure Mail Washer to delete black listed emails at the server and only download the white listed emails to your computer.
Which is better? Delete in the server? or Delete in the computer?
What will you do if you don't have the Mail Washer? you will download all mails including SPAM to your computer. So you are wasting your internet time and bandwidth. You also waste time by opening these spam mails and deleting them manually. Some spam emails also have 'web bugs' that can spy on you and send your secrets to the web bugs creator.
Using Mail Washer you can identify SPAM mails at the server and delete it there itself. Web bugs will not function. Only good emails will be downloaded to your computer. So you save on your internet time, bandwidth and your time and money.
 9:47 PM
9:47 PM
 File Under :
Informative
File Under :
Informative
You can become a great artist by using computer. The computer provides paint, brush, and canvas to create an image based on your imagination. It makes not only pictures and also makes map, logo wallpaper, and letterhead as you like. For this, you use Photoshop, Corel draw painting software’s. You will buy these software’s or to use equaling share ware programs like paint shop pro etc. For compare to this the free painting programs have less facilities. You can download these free painting programs from Internet.
If you enter Crayola websites you can draw the pictures and enjoy it. Windows operating system have free painting program. That is MS Paint. You can use this to draw the pictures. To open the MS Paint click Start => Programs => Accessories => Paint. Now we have a paint program. The Canvas placed center in this. You are drawing in this canvas. The Toolbox is left side in this canvas. Toolbox has more tools for drawing. Below in the canvas have more colors part. That is a Color Palette. The Menu Bar is above in the canvas.
To Change Canvas Size:
You decide that can you draw the picture in displaying canvas. If you cannot draw that, change the canvas size for any unit like inches, centimeter, and pixel. To change the canvas size click Image Attribute. Type length and width then click OK.
We can use two colors at a time in MS painting program. One is background color another one color is to use drawing in foreground. These two colors are in color palette starting. To change the foreground colors to left click any color in color palette. Now you can see color changed in color palette starting. To change background color to right clicks any color in color palette. If you draw to pressing left click the drawing have background color. If you draw to pressing right click the drawing have background.
Now the canvas and colors are ready then we start to draw the picture. For using in this, the MS Paint gives more tools. If you place mouse in any tool that give a tool name. The MS Paint gives more tools to use drawing. These are Pencil, Brush, Air Brush, Line Curve, Rectangle, Polygon, Ellipse and Rounded Rectangle. If you click one tool more sub tools display below in that tool. It denotes that tools size. For example if you clock Line tool, we have different lines depends upon width to use drawing. We can change the tool that tool size at any time. If you draw wrongly, you can erase that to use Eraser tool. It’s had some different sizes. If you want to type Text in picture to click Text tool and make a rectangle in canvas. Then you can type letter in that rectangle. You can change letter font, size and style.
If you use Rectangle and Ellipse tools, to press these tools with shift key we get square, rectangle respectively. Same as that to press shift key with Rounded Rectangle tool we get rounded square. We want to fill the color in closed object to use Fill with Color tool.
If you want only one part to maximize for painting, you click Magnifier tool then click that part. Now that part is to maximized. If you want to change part size to normal to click Magnifier tool than click that part. The MS Paint gives Free Form Select and Rectangle Select tools to select one part in picture. The Rectangle Select tool used to select square/Rectangle, the Free Form Select to use select other shapes. Then give Edit Copy command, now that part is copy to clipboard. After that you can paste this in any place. If you want to change foreground color to a particular color then click Pick Color tool and then click particular part. This tool is also called as Eye Dropper.
To save the Picture:
We can save the picture to BMP format in MS Paint. BMP means Bitmap. The windows 98-second edition and other edition released after that have BMP, GIF, and JPEG Formats.
To give special effects:
If you click Image menu you got a more commands. We can rotate the pictures, invert the picture, and enlarge the picture like rubber, to slope the picture. You can use this facility for your drawing and became a great artist.
If you enter Crayola websites you can draw the pictures and enjoy it. Windows operating system have free painting program. That is MS Paint. You can use this to draw the pictures. To open the MS Paint click Start => Programs => Accessories => Paint. Now we have a paint program. The Canvas placed center in this. You are drawing in this canvas. The Toolbox is left side in this canvas. Toolbox has more tools for drawing. Below in the canvas have more colors part. That is a Color Palette. The Menu Bar is above in the canvas.
To Change Canvas Size:
You decide that can you draw the picture in displaying canvas. If you cannot draw that, change the canvas size for any unit like inches, centimeter, and pixel. To change the canvas size click Image Attribute. Type length and width then click OK.
We can use two colors at a time in MS painting program. One is background color another one color is to use drawing in foreground. These two colors are in color palette starting. To change the foreground colors to left click any color in color palette. Now you can see color changed in color palette starting. To change background color to right clicks any color in color palette. If you draw to pressing left click the drawing have background color. If you draw to pressing right click the drawing have background.
Now the canvas and colors are ready then we start to draw the picture. For using in this, the MS Paint gives more tools. If you place mouse in any tool that give a tool name. The MS Paint gives more tools to use drawing. These are Pencil, Brush, Air Brush, Line Curve, Rectangle, Polygon, Ellipse and Rounded Rectangle. If you click one tool more sub tools display below in that tool. It denotes that tools size. For example if you clock Line tool, we have different lines depends upon width to use drawing. We can change the tool that tool size at any time. If you draw wrongly, you can erase that to use Eraser tool. It’s had some different sizes. If you want to type Text in picture to click Text tool and make a rectangle in canvas. Then you can type letter in that rectangle. You can change letter font, size and style.
If you use Rectangle and Ellipse tools, to press these tools with shift key we get square, rectangle respectively. Same as that to press shift key with Rounded Rectangle tool we get rounded square. We want to fill the color in closed object to use Fill with Color tool.
If you want only one part to maximize for painting, you click Magnifier tool then click that part. Now that part is to maximized. If you want to change part size to normal to click Magnifier tool than click that part. The MS Paint gives Free Form Select and Rectangle Select tools to select one part in picture. The Rectangle Select tool used to select square/Rectangle, the Free Form Select to use select other shapes. Then give Edit Copy command, now that part is copy to clipboard. After that you can paste this in any place. If you want to change foreground color to a particular color then click Pick Color tool and then click particular part. This tool is also called as Eye Dropper.
To save the Picture:
We can save the picture to BMP format in MS Paint. BMP means Bitmap. The windows 98-second edition and other edition released after that have BMP, GIF, and JPEG Formats.
To give special effects:
If you click Image menu you got a more commands. We can rotate the pictures, invert the picture, and enlarge the picture like rubber, to slope the picture. You can use this facility for your drawing and became a great artist.
Monday, September 29, 2008
 5:31 PM
5:31 PM
 File Under :
Informative
File Under :
Informative
Here’s a nifty little trick for creating a text file listing of the contents of a folder, without using any extra software. Step one is to note down the path and name of the folder concerned; if it’s a long one, click on the folder icon in Windows Explorer so that it’s displayed in the address box, then right-click on it and select Copy. Now open a command window by going to Run (XP) or Search (Vista) on the Start menu and type ‘cmd’
A DOS like window opens and at the flashing prompt type cd then a space and type in the path and name of the folder – in my example the folder is called ‘Pix’, so the first line looks like this:
cd C:\Pix
If you used the Copy trick simply right-click on the flashing prompt and select Paste.
Now press Enter and the cd (change directory) command changes the display to show the path and name of your folder, thus:
C:\Pix>
Now at the flashing command prompt type the following:
dir /b > c:\listfolder.txt
Press Enter and a file called listfolder.text appears in the root directory of your C: drive; open it in Word or double click on it and Notepad displays a text file listing the contents of your chosen folder.
For those who may be interested, ‘dir’ is the Directory list command, ‘/b’ tells it to omit the file’s time, date and size information and the forward arrow or greater than symbol (>) tells it to send the information into the file called listfolder.text
A DOS like window opens and at the flashing prompt type cd then a space and type in the path and name of the folder – in my example the folder is called ‘Pix’, so the first line looks like this:
cd C:\Pix
If you used the Copy trick simply right-click on the flashing prompt and select Paste.
Now press Enter and the cd (change directory) command changes the display to show the path and name of your folder, thus:
C:\Pix>
Now at the flashing command prompt type the following:
dir /b > c:\listfolder.txt
Press Enter and a file called listfolder.text appears in the root directory of your C: drive; open it in Word or double click on it and Notepad displays a text file listing the contents of your chosen folder.
For those who may be interested, ‘dir’ is the Directory list command, ‘/b’ tells it to omit the file’s time, date and size information and the forward arrow or greater than symbol (>) tells it to send the information into the file called listfolder.text
 5:30 PM
5:30 PM
 File Under :
Informative
File Under :
Informative
Rapidshare is one of the most frustrating websites to download large files off of, especially if they are broken into many pieces while Megaupload positively shines in comparison. So why do people keep using these two services when more generous file hosts like Mediafire exist?
I can only guess that it’s simply because so many other people are using them. In order to get free premium Rapidshare accounts, which let you download unlimited amounts of files, users upload their own files onto Rapidshare, hoping enough people download them in turn so that the uploaders can earn enough premium points to qualify for a free account.
But it doesn’t have to be that complicated. You can get unlimited Rapidshare downloads more simply.
What you are going to do is request a new IP address from your ISP. This is assuming that you do not subscribe to an Internet service with fixed IP addresses.
First, figure out what your current IP address is by going to IP Chicken. Write down the series of numbers that are displayed. This is your current IP address.
Then, follow the steps below to get a new IP:
1. Go to Start->Run and type in “cmd” without quotes to bring up the command prompt. Hit Enter.
2. Type in “ipconfig /flushdns” without quotes and hit Enter.
3. Type in “ipconfig /release” without quotes and hit Enter.
4. Type in “ipconfig /renew” without quotes and hit Enter. You should now have a new IP address. Check your IP address at IP Chicken again and compare it to the one you got earlier.
5. Now, erase your browser’s cache and cookies.
6. Try downloading the Rapidshare or Megaupload file again.
I can only guess that it’s simply because so many other people are using them. In order to get free premium Rapidshare accounts, which let you download unlimited amounts of files, users upload their own files onto Rapidshare, hoping enough people download them in turn so that the uploaders can earn enough premium points to qualify for a free account.
But it doesn’t have to be that complicated. You can get unlimited Rapidshare downloads more simply.
What you are going to do is request a new IP address from your ISP. This is assuming that you do not subscribe to an Internet service with fixed IP addresses.
First, figure out what your current IP address is by going to IP Chicken. Write down the series of numbers that are displayed. This is your current IP address.
Then, follow the steps below to get a new IP:
1. Go to Start->Run and type in “cmd” without quotes to bring up the command prompt. Hit Enter.
2. Type in “ipconfig /flushdns” without quotes and hit Enter.
3. Type in “ipconfig /release” without quotes and hit Enter.
4. Type in “ipconfig /renew” without quotes and hit Enter. You should now have a new IP address. Check your IP address at IP Chicken again and compare it to the one you got earlier.
5. Now, erase your browser’s cache and cookies.
6. Try downloading the Rapidshare or Megaupload file again.
 5:28 PM
5:28 PM
 File Under :
Informative
File Under :
Informative
If you’re preparing to reinstall an operating system (for example, doing a clean install of Windows XP) or an application like Microsoft Office, you will need to find your copy of the software’s product key (CD key). Normally this product key is located with the manual or CD that came with your software.
If you’ve lost your product key you can often times find it in the registry but this can be very difficult to impossible to retrieve manually. Luckily, there are many free key finder programs available to help.
Below are the top 3 free key finder programs.
more and source:
http://pcsupport.about.com/
If you’ve lost your product key you can often times find it in the registry but this can be very difficult to impossible to retrieve manually. Luckily, there are many free key finder programs available to help.
Below are the top 3 free key finder programs.
more and source:
http://pcsupport.about.com/
Sunday, September 28, 2008
Some quick tips to get your iPhone skills slicker than the guy or girl next door. To rearrange the icons on the home page, tap and hold any icon until all the icons start to giggle. Now you can drag icons about, including on and off the Dock or between pages. Click the Home button to lock the icons again. The Dock is limited to four icons but, if you set the Home button’s double-click to call up your Contact favourites, you can remove the Phone icon from the Dock.
If you manage to crash your iPhone 3G playing with third-party apps, hold both the power and home buttons for 10 seconds to reboot the phone. Recalcitrant apps can be uninstalled using Installer.
Apple originally charged for custom ringtones but now you can create your own in GarageBand, while Windows users can follow the video tutorial at . SendSong supposedly lets you add any track in your iPod playlist to the custom ringtone list under Settings/Sounds/Ringtone, but we couldn’t get any love from it.
When using Safari, you need to rotate the phone *before* calling up the keyboard. Safari has a useful “.com” button, but you can add international domain extensions by enabling extra languages under General/Keyboards/International Keyboards. Back at the Safari keyboard, use the globe key to toggle through languages. Now when you press “.com”, drag your finger up to get extra options. Our iPhone 3G review unit from Optus surprisingly didn’t feature an Australian keyboard with .com.au, but for a first-gen iPhone there’s a hack for adding com.au at http://www.linka.co.nz/iphone_keyboard.php
Many of the GSM command codes also work on the iPhone. There’s a good list at but *3001#12345#* is handy for viewing network and cell information.
If you manage to crash your iPhone 3G playing with third-party apps, hold both the power and home buttons for 10 seconds to reboot the phone. Recalcitrant apps can be uninstalled using Installer.
Apple originally charged for custom ringtones but now you can create your own in GarageBand, while Windows users can follow the video tutorial at . SendSong supposedly lets you add any track in your iPod playlist to the custom ringtone list under Settings/Sounds/Ringtone, but we couldn’t get any love from it.
When using Safari, you need to rotate the phone *before* calling up the keyboard. Safari has a useful “.com” button, but you can add international domain extensions by enabling extra languages under General/Keyboards/International Keyboards. Back at the Safari keyboard, use the globe key to toggle through languages. Now when you press “.com”, drag your finger up to get extra options. Our iPhone 3G review unit from Optus surprisingly didn’t feature an Australian keyboard with .com.au, but for a first-gen iPhone there’s a hack for adding com.au at http://www.linka.co.nz/iphone_keyboard.php
Many of the GSM command codes also work on the iPhone. There’s a good list at but *3001#12345#* is handy for viewing network and cell information.
 5:33 PM
5:33 PM
 File Under :
Informative
File Under :
Informative
From the moment you start using Windows Vista, you’ll find a lot of new things to get used to: new programs, new layout, new ways of doing things. Some are great, some are confusing, some are just very well hidden. These are my picks for the 19 things you should try when you first start using Windows Vista do you think differently?
1. Use Flip3D
Okay, so it’s hardly essential, but it’s still one of the first things you should try: it’s just a neat way to show off that snazzy new interface. Hold down the Windows key and your keyboard and hit Tab to spool through them.
2. Fix a photo - and automatically back it up
One of the most useful new programs, Photo Gallery enables you to automatically import and organise your photos. Click Fix and you can crop out unsightly backgrounds, remove red-eye and adjust the lighting, too. But the most impressive feature is that it automatically backs up every photo: press CTRL and R and it’ll restore it just as it was when you first imported it.
3. Launch any program instantly
Want to open something even faster? Hold down the Windows key and press a number from 1 to 9, and it’ll open the corresponding entry in the Quick Start menu next to the Start button.
Windows and 1 opens the shortcut next to the button (usually Show Desktop), Windows and 2 opens the second shortcut (usually Flip 3D) and so on. To add or rearrange shortcuts, just click and drag them.
4. Save time browsing your folder
Are you regularly digging through your hard drive to open the same folder? Click and drag it into the Favorite Links pane on the left of every Windows Explorer window to keep it just one click away.
5. Get more from your laptop
If you’re running Windows Vista on a mobile PC, hold down the Windows key and press X to open up the new Mobility Center. It gives instant access to controls for the battery, wireless signal, external displays and more.
6. Add a gadget to your desktop
That new strip on the side of your desktop is more useful thank you might think: click the plus symbol at the top, then click Get more gadgets online to view the 370+ (and counting) free downloads that add instant new features to your desktop - everything from BBC radio to currency conversion. You can drag and drop them on to the desktop, too - the Weather gadget, for example, is actually more useful when used like this because it gives you a three day forecast.
7. Make search even easier
The built-in search can find things even if you don’t remember what they’re called. Open your Documents window, click Organise > Folder and Search options, select the Search tab and click “use natural language search.” You can now search for things like “photo taken last week” or “email sent from Dave” and it’ll bring back all matching results.
8. Connect to other laptops
If you’ve got a wireless laptop, you can quickly create a network with others by opening up Meeting Space. Create a display name, click Start a new meeting, and see if says Using: Ad Hoc Wireless Network on the bottom right. If not, click Options and tick the appropriate box. Then all you’ve got to do is enter a password and click the green button to create it. Other laptops nearby can join by loading Meeting Space and clicking Join a meeting near me. Once in, click Add a handout to share a file or Share a program or desktop to - wait for it - share a program or your PC’s desktop.
9. Protect your files
Backing up your files is given the importance it deserves in Windows Vista - particularly compared to the crude and mostly-hidden tool in Windows XP - and it’s ever so easy to use. Open Backup and Restore Center from the Start menu, hit Back Up Files and choose if you want to back up photos, email, music and more: they’ll be automatically saved to your choice of backup device. Got Windows XP backups you want to add to your Windows Vista PC? You can import them by using this tool.
10. Get the old power button back
One of the neater new features in Windows Vista is that the Power button on the Start menu doesn’t turn your PC off - it puts it into a new low-power state, so it’s all but deactivated but is much quicker to start up. If you don’t want to use this - or you’ve got an older PC that doesn’t support it properly - you can change it by digging deep in the configuration options. Search for “power” in the Start Menu and clicking Power Options. Click Change plan settings, then Change advanced power settings and expand the entry for Power buttons and lid. Expand Start menu and power button entry and click on Sleep to pick another option from the drop-down menu.
11. Zoom in on your desktop
Open any Windows Explorer window, select an icon, hold down CTRL and scroll your mouse wheel - and your icons will expand before your eyes. It makes them easier to view, and as nearly every icon is a snapshot of the file itself, you can see what’s inside them as well.
12. Check your PC’s health
Troubleshooting has got a whole lot easier with Windows Vista’s reporting tools. Search for “perf” in the Control Panel, click Performance Information and Tools, and then select Advanced tools from the list on the left. Click the Generate a system health report option at the bottom of the list and it’ll give you a list of any problems with your PC and what you can do to fix them.
13. View files without opening them
In Windows Explorer, click Organise > Layout and select Preview Pane. You’ll get an extra panel on the right of every window that shows you the contents of every file: if it’s a PowerPoint presentation, you can click through the slides too.
14. Try Media Center
If you’ve never used Media Center before, you’re in for a treat. Formerly a separate version of Windows, it’s now supplied as standard in Windows Vista Home Premium and Windows Vista Ultimate, giving you a new way to enjoy your photos, music and TV. Hook it up to your telly - which you can do with ease by connecting an Xbox 360 to your home network - and you can easily set up recording of TV programmes and pause live TV.
15. Get your old programs working
Most programs work fine with Windows Vista, but older releases can have problems. If you can’t get an older release working properly, search for “compat” in the Control Panel and click on Use an older program with this version of Windows. This will lead you through the required steps if the program in question worked in Windows XP, check the options for Windows XP Service Pack 2 and Run as administrator.
16. Create a search folder
If you’re regularly looking for the same thing, save the search. Click the Save Search button in the Explorer window and it’ll create a Search Folder of all the items that match that search. To make it even easier to find, select the Searches entry in the Favorite links sidebar on the left, and then drag your newly created folder into the Favorite Links list.
17. Get your old menus back
Are you missing File, Edit, View and the other old stagers from Windows Explorer in Windows XP? Just press Alt and they’ll appear.
18. Try tablet input
Another former exclusive now supplied with Windows Vista Home Premium and Windows Vista Ultimate, tablet input is a new way to control your PC. Handiest for desktop users is the Snipping Tool; open it and you can drag the mouse to snap a screenshot. If you want to replace the keyboard, search for “tablet” in the Start menu and fire up the Tablet PC Input Panel - you’ll need a stylus to make the most of it, though.
19. Adjust your security settings
As you’ll have noticed when using the tips above, the new security features in Windows Vista are very keen, prompting you every time you access a system feature. It’s a very effective way of keeping the bad guys out, and I really recommend leaving it in place - but if you fancy your chances at protecting yourself, you can turn it off by clicking your user icon at the top of the Start menu and choosing Turn User Account Control on or off.
1. Use Flip3D
Okay, so it’s hardly essential, but it’s still one of the first things you should try: it’s just a neat way to show off that snazzy new interface. Hold down the Windows key and your keyboard and hit Tab to spool through them.
2. Fix a photo - and automatically back it up
One of the most useful new programs, Photo Gallery enables you to automatically import and organise your photos. Click Fix and you can crop out unsightly backgrounds, remove red-eye and adjust the lighting, too. But the most impressive feature is that it automatically backs up every photo: press CTRL and R and it’ll restore it just as it was when you first imported it.
3. Launch any program instantly
Want to open something even faster? Hold down the Windows key and press a number from 1 to 9, and it’ll open the corresponding entry in the Quick Start menu next to the Start button.
Windows and 1 opens the shortcut next to the button (usually Show Desktop), Windows and 2 opens the second shortcut (usually Flip 3D) and so on. To add or rearrange shortcuts, just click and drag them.
4. Save time browsing your folder
Are you regularly digging through your hard drive to open the same folder? Click and drag it into the Favorite Links pane on the left of every Windows Explorer window to keep it just one click away.
5. Get more from your laptop
If you’re running Windows Vista on a mobile PC, hold down the Windows key and press X to open up the new Mobility Center. It gives instant access to controls for the battery, wireless signal, external displays and more.
6. Add a gadget to your desktop
That new strip on the side of your desktop is more useful thank you might think: click the plus symbol at the top, then click Get more gadgets online to view the 370+ (and counting) free downloads that add instant new features to your desktop - everything from BBC radio to currency conversion. You can drag and drop them on to the desktop, too - the Weather gadget, for example, is actually more useful when used like this because it gives you a three day forecast.
7. Make search even easier
The built-in search can find things even if you don’t remember what they’re called. Open your Documents window, click Organise > Folder and Search options, select the Search tab and click “use natural language search.” You can now search for things like “photo taken last week” or “email sent from Dave” and it’ll bring back all matching results.
8. Connect to other laptops
If you’ve got a wireless laptop, you can quickly create a network with others by opening up Meeting Space. Create a display name, click Start a new meeting, and see if says Using: Ad Hoc Wireless Network on the bottom right. If not, click Options and tick the appropriate box. Then all you’ve got to do is enter a password and click the green button to create it. Other laptops nearby can join by loading Meeting Space and clicking Join a meeting near me. Once in, click Add a handout to share a file or Share a program or desktop to - wait for it - share a program or your PC’s desktop.
9. Protect your files
Backing up your files is given the importance it deserves in Windows Vista - particularly compared to the crude and mostly-hidden tool in Windows XP - and it’s ever so easy to use. Open Backup and Restore Center from the Start menu, hit Back Up Files and choose if you want to back up photos, email, music and more: they’ll be automatically saved to your choice of backup device. Got Windows XP backups you want to add to your Windows Vista PC? You can import them by using this tool.
10. Get the old power button back
One of the neater new features in Windows Vista is that the Power button on the Start menu doesn’t turn your PC off - it puts it into a new low-power state, so it’s all but deactivated but is much quicker to start up. If you don’t want to use this - or you’ve got an older PC that doesn’t support it properly - you can change it by digging deep in the configuration options. Search for “power” in the Start Menu and clicking Power Options. Click Change plan settings, then Change advanced power settings and expand the entry for Power buttons and lid. Expand Start menu and power button entry and click on Sleep to pick another option from the drop-down menu.
11. Zoom in on your desktop
Open any Windows Explorer window, select an icon, hold down CTRL and scroll your mouse wheel - and your icons will expand before your eyes. It makes them easier to view, and as nearly every icon is a snapshot of the file itself, you can see what’s inside them as well.
12. Check your PC’s health
Troubleshooting has got a whole lot easier with Windows Vista’s reporting tools. Search for “perf” in the Control Panel, click Performance Information and Tools, and then select Advanced tools from the list on the left. Click the Generate a system health report option at the bottom of the list and it’ll give you a list of any problems with your PC and what you can do to fix them.
13. View files without opening them
In Windows Explorer, click Organise > Layout and select Preview Pane. You’ll get an extra panel on the right of every window that shows you the contents of every file: if it’s a PowerPoint presentation, you can click through the slides too.
14. Try Media Center
If you’ve never used Media Center before, you’re in for a treat. Formerly a separate version of Windows, it’s now supplied as standard in Windows Vista Home Premium and Windows Vista Ultimate, giving you a new way to enjoy your photos, music and TV. Hook it up to your telly - which you can do with ease by connecting an Xbox 360 to your home network - and you can easily set up recording of TV programmes and pause live TV.
15. Get your old programs working
Most programs work fine with Windows Vista, but older releases can have problems. If you can’t get an older release working properly, search for “compat” in the Control Panel and click on Use an older program with this version of Windows. This will lead you through the required steps if the program in question worked in Windows XP, check the options for Windows XP Service Pack 2 and Run as administrator.
16. Create a search folder
If you’re regularly looking for the same thing, save the search. Click the Save Search button in the Explorer window and it’ll create a Search Folder of all the items that match that search. To make it even easier to find, select the Searches entry in the Favorite links sidebar on the left, and then drag your newly created folder into the Favorite Links list.
17. Get your old menus back
Are you missing File, Edit, View and the other old stagers from Windows Explorer in Windows XP? Just press Alt and they’ll appear.
18. Try tablet input
Another former exclusive now supplied with Windows Vista Home Premium and Windows Vista Ultimate, tablet input is a new way to control your PC. Handiest for desktop users is the Snipping Tool; open it and you can drag the mouse to snap a screenshot. If you want to replace the keyboard, search for “tablet” in the Start menu and fire up the Tablet PC Input Panel - you’ll need a stylus to make the most of it, though.
19. Adjust your security settings
As you’ll have noticed when using the tips above, the new security features in Windows Vista are very keen, prompting you every time you access a system feature. It’s a very effective way of keeping the bad guys out, and I really recommend leaving it in place - but if you fancy your chances at protecting yourself, you can turn it off by clicking your user icon at the top of the Start menu and choosing Turn User Account Control on or off.
 5:31 PM
5:31 PM
 File Under :
Informative
File Under :
Informative
After the release of Firefox 2.0, the memory leak has become an even more notorious problem than before. On average, Firefox should take up no more than 80MB of RAM. Any more than that and you can consider yourself a victim of Firefox’s memory leak. I’m sure you’ve probably already seen a ton of guides on how to fix the memory leak problem in Firefox already. The reason why I’m writing another one on Vista Rewired is because none of those have worked very well for me. This one will be a little different because I’ve added a few of my ingredients in.
Just to give you a heads-up, this guide is going to be quite long but it’ll cover everything you need to know.
Before we do anything, make sure you have the newest version of Firefox. If you don’t have the latest version, you can
1) Check your extensions and themes:
The most common cause for high memory usage for Firefox usually lies in the extensions and themes. If you overloaded your Firefox with extensions, you can expect high memory usage. Uninstall the ones you don’t need, and update all the ones you will be using. After that, you’ll first want to consult this list of problematic extensions that could be causing the problem. Make sure none of the extensions you are running are on that list.
After comparing with that list, if you still have the problem, it could be the result of a newly installed theme or extension. Experiment with shutting down suspicious extensions or switching themes.
2) Start Firefox in Safe Mode
If one of your extensions is not in that list, boot Firefox into Safe Mode to disable all extensions and themes. You can do this by going to Start > Run, and entering:
firefox -safe-mode
A box similar to the one below should appear.
Check Disable all add-ons, then select Continue in Safe Mode. Now, compare the RAM usage of when Firefox had it’s add-ons enabled and when they were disabled.
You can expect a difference of a couple megabytes since the extensions have been disabled. But if you notice a large difference in RAM usage, this may suggest a problem within your extensions or theme.
Just to give you a heads-up, this guide is going to be quite long but it’ll cover everything you need to know.
Before we do anything, make sure you have the newest version of Firefox. If you don’t have the latest version, you can
1) Check your extensions and themes:
The most common cause for high memory usage for Firefox usually lies in the extensions and themes. If you overloaded your Firefox with extensions, you can expect high memory usage. Uninstall the ones you don’t need, and update all the ones you will be using. After that, you’ll first want to consult this list of problematic extensions that could be causing the problem. Make sure none of the extensions you are running are on that list.
After comparing with that list, if you still have the problem, it could be the result of a newly installed theme or extension. Experiment with shutting down suspicious extensions or switching themes.
2) Start Firefox in Safe Mode
If one of your extensions is not in that list, boot Firefox into Safe Mode to disable all extensions and themes. You can do this by going to Start > Run, and entering:
firefox -safe-mode
A box similar to the one below should appear.
Check Disable all add-ons, then select Continue in Safe Mode. Now, compare the RAM usage of when Firefox had it’s add-ons enabled and when they were disabled.
You can expect a difference of a couple megabytes since the extensions have been disabled. But if you notice a large difference in RAM usage, this may suggest a problem within your extensions or theme.
Saturday, September 27, 2008
 5:40 PM
5:40 PM
 File Under :
Informative
File Under :
Informative
Firefox is in my opinion the best browser ever made until now. It includes:
-improved tabbed browsing
-pop up blocking
-integrated Goggle search
-enhanced privacy controls
-built-in phishing protection
-online spell checking
-lots of themes, interfaces, and extensions/addons
Mozilla Firefox officially supports:
-Microsoft Windows
-Linux
-Mac OS X
Unofficial Support:
-Free BSD
-OS/2
-Solaris
-SkyOS
-BeOS
-XP Professional x64 Edition
Now here are some Tips&Tricks that can help you double the speed of Firefox.
1. Type about:config in the address bar and then press Enter.

2. In the filter search bar type network.http.pipelining. Be sure the value field is set true,if not double-click to set true.

HTTP is the application-layer protocol that most web pages are transferred with. In HTTP 1.1, multiple requests can be sent before any responses are received. This is known as pipelining. Pipelining reduces page loading times, but not all servers support it.
3. Go back to the filter search bar and type network.http.pipelining.maxrequests. Double-click this option and set its value to 8.

4. In the filter search bar and type network.http.proxy.pipelining. Once opened double-click on it and set it to true.

5. In IPv6-capable DNS servers, an IPv4 address may be returned when an IPv6 address is requested. It is possible for Mozilla to recover from this misinformation, but a significant delay is introduced.
Type network.dns.disableIPv6 in the filter search bar and set this option to true by double clicking on it.

6. CONTENT INTERRUPT PARSING
This preference controls if the application will interrupt parsing a page to respond to UI events. It does not exist by default.
Right-click (Apple users ctrl-click) anywhere in the about:config window, select New and then Boolean from the pop-up menu. Then:

A. Enter content.interrupt.parsing in the New boolean value pop-up window and click OK

B. When prompted to choose the value for the new boolean, select true and click OK.

-improved tabbed browsing
-pop up blocking
-integrated Goggle search
-enhanced privacy controls
-built-in phishing protection
-online spell checking
-lots of themes, interfaces, and extensions/addons
Mozilla Firefox officially supports:
-Microsoft Windows
-Linux
-Mac OS X
Unofficial Support:
-Free BSD
-OS/2
-Solaris
-SkyOS
-BeOS
-XP Professional x64 Edition
Now here are some Tips&Tricks that can help you double the speed of Firefox.
1. Type about:config in the address bar and then press Enter.

2. In the filter search bar type network.http.pipelining. Be sure the value field is set true,if not double-click to set true.

HTTP is the application-layer protocol that most web pages are transferred with. In HTTP 1.1, multiple requests can be sent before any responses are received. This is known as pipelining. Pipelining reduces page loading times, but not all servers support it.
3. Go back to the filter search bar and type network.http.pipelining.maxrequests. Double-click this option and set its value to 8.

4. In the filter search bar and type network.http.proxy.pipelining. Once opened double-click on it and set it to true.

5. In IPv6-capable DNS servers, an IPv4 address may be returned when an IPv6 address is requested. It is possible for Mozilla to recover from this misinformation, but a significant delay is introduced.
Type network.dns.disableIPv6 in the filter search bar and set this option to true by double clicking on it.

6. CONTENT INTERRUPT PARSING
This preference controls if the application will interrupt parsing a page to respond to UI events. It does not exist by default.
Right-click (Apple users ctrl-click) anywhere in the about:config window, select New and then Boolean from the pop-up menu. Then:

A. Enter content.interrupt.parsing in the New boolean value pop-up window and click OK

B. When prompted to choose the value for the new boolean, select true and click OK.

 5:38 PM
5:38 PM
 File Under :
Informative
File Under :
Informative
If you use a 64-bit version of Windows Vista on a computer with multiple processors or on a multi-core (dual-core, quad-core) processor (which is quite usual), you can use a simple setting to accelerate booting of the computer (OS).
Depending on the configuration of your computer, this setting may result in a smaller or substantial improving of the Windows booting time. Please be aware that this setting is not intended for novice users and it can cause booting problems on incompatible (mostly “noname”) computers.
By default, Vista detects and switches to a multi-processor core only after the basic functions of Windows are loaded - for actual booting it uses only a single core (logical processor). With the following setting you will enable using of all available cores/processors also for booting.
Run the MSCONFIG command (Start > Run) and go to the “Boot” tab. There click the “Advanced options” button. In the “BOOT advance options” dialog check the “Number of processors” option and set the number of processor cores you have available in your PC. Exit the command with OK. The following restart should be faster.
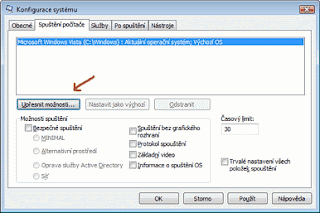
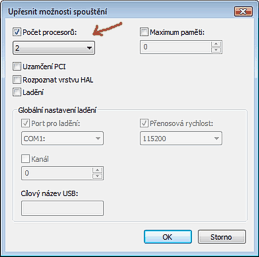
This setting is sometimes considered as a hoax (myth) but it seems to really help in many cases - so try it yourself.
Depending on the configuration of your computer, this setting may result in a smaller or substantial improving of the Windows booting time. Please be aware that this setting is not intended for novice users and it can cause booting problems on incompatible (mostly “noname”) computers.
By default, Vista detects and switches to a multi-processor core only after the basic functions of Windows are loaded - for actual booting it uses only a single core (logical processor). With the following setting you will enable using of all available cores/processors also for booting.
Run the MSCONFIG command (Start > Run) and go to the “Boot” tab. There click the “Advanced options” button. In the “BOOT advance options” dialog check the “Number of processors” option and set the number of processor cores you have available in your PC. Exit the command with OK. The following restart should be faster.


This setting is sometimes considered as a hoax (myth) but it seems to really help in many cases - so try it yourself.
 5:38 PM
5:38 PM
 File Under :
Informative
File Under :
Informative
Following the release of Internet Explorer 8 Beta 2 at the end of August 2008, Microsoft offered a toolset designed to permit advanced customization of the browser. Internet Explorer Administration Kit 8.0 Beta was dropped after the English, Japanese, Chinese (Simplified), and German localized versions of IE8. On September 16, the kit was updated to reflect the wave 2 of Internet Explorer 8 Beta 2 releases. Earlier this week Microsoft made available 21 new fully localized flavors of IE8 Beta 2, bringing the total number of language versions to 25. “With the release of these additional languages, the IE8 IEAK can now build an additional 20 language packages. We’re excited to enable more users to download IE8 Beta 2 and use it in their native languages,” revealed Vishwac Sena Kannan, IE international program manager. The September 16 release of Internet Explorer Administration...
Friday, September 26, 2008
 5:29 PM
5:29 PM
 File Under :
Informative
File Under :
Informative
Here’s a nifty little Windows XP trick that lets you quickly preview multimedia files (AVI, CD Audio, MP3 etc.) in Windows Explorer, without having to wait for Windows Medial Player or your chosen media player to open. All you have to do is open Windows Explorer then go to Tools > Folder Options and select the File Types tab. Scroll down the list and click to highlight the multimedia file type you want to be able to preview. e.g. avi movie files, then click the Advanced button then New. In the Action box give the function a name, i.e. ‘Quickview’ then in the ‘Application used to perform action’ box copy and paste the following command:
C:\Windows\System32\Mplay32.exe /Play %1
Click OK to exit the dialogue boxes and it’s done. Now in Windows Explorer find an avi file (or your chosen file type), on the menu that appears select Quickview and the file will immediately start playing.
C:\Windows\System32\Mplay32.exe /Play %1
Click OK to exit the dialogue boxes and it’s done. Now in Windows Explorer find an avi file (or your chosen file type), on the menu that appears select Quickview and the file will immediately start playing.
 5:27 PM
5:27 PM
 File Under :
Informative
File Under :
Informative

Sooner or later most of us have to confront the problem of running out of hard disc space. Usually there’s no alternative but to bite the bullet and delete some files and applications, upgrade to a larger hard drive, install a second hard drive, or if the PC is coming to the end of the road, buy a new one. However, it may be possible to delay the inevitable by scanning your drive with this freeware utility. It’s called DoubleKiller and its job is to track down and eradicate duplicate files. You would probably be surprised how many duplicate files you accumulate over time, I found several hundred megabytes worth on a quite modestly well-used office PC. It’s a stand-alone program, so it doesn’t have to be installed on your PC, and it is very easy to use, and very safe too as you can specify exactly which types of files to look for, and manually or automatically select the files to be deleted.
 5:26 PM
5:26 PM
 File Under :
Informative
File Under :
Informative

Whenever Windows stumbles across a file type it doesn’t recognise you are will see a message box that says Windows cannot open this file’ and gives you the option to ‘Use the Web Service’, to find the necessary program. I don’t know about you but I can’t recall a single instance where it has worked and it’s usually much quicker just to Google the file name or extension. Well, thanks to the clever folk at ‘howtogeek’ here’s a way to zap that dialogue box and go straight to the Programs list, that you would get if you chose the second option. It works in both XP and Vista and involves editing the Registry, so pay attention, and bear in mind the usual warnings and disclaimers about backing up the Registry first, and not messing with it if you don’t know what you are doing.
Begin by opening the Registry Editor (‘regedit’ in Run on the Start menu) and pop along to: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Policies\
If there is a key called Explorer skip the next step, if not create one by right-click Policies then New > Key and rename it ‘Explorer’ (without the quotes). The Explorer key should now be open in the right hand pane, right click into it and select New > DWORD Value, rename that to: ‘NoInternetOpenWith’, right-click it, select Modify and change the Value to 1. (Changing the Value to 0, or deleting the key will reset the hack). That’s it, close Regedit, there’s no need for a reboot, so all that remains is to try it out by creating a file with an unrecognised extension and see what happens whenyou try to open it.
Thursday, September 25, 2008
 5:32 PM
5:32 PM
 File Under :
Tips And Tricks
File Under :
Tips And Tricks
If you get the error: "Error Number: OX80070725 / Description: Incompatible version of the RPC setup. Setup will terminate" while trying to install a game into my windows PC then the reason for this is that OLEAut 32.dll, OLDPRO32.DLL, ASYCFILT.DLL or such files are corrupt or incompatible.
To solve this problem, goto the Windows site at
http://download.microsoft.com/download/msninvestor/patch/1.0/win98/en-us/mcrepair.exe and download the .EXE file and install. While installing, you maybe prompted whether you want to replace the old files with the new files confirm 'Yes'. After that install the game and enjoy.
If you want to read more about this error from Microsoft, you can do so at this page:
http://support.microsoft.com/default.aspx?scid=kb;en-us;321915
To solve this problem, goto the Windows site at
http://download.microsoft.com/download/msninvestor/patch/1.0/win98/en-us/mcrepair.exe and download the .EXE file and install. While installing, you maybe prompted whether you want to replace the old files with the new files confirm 'Yes'. After that install the game and enjoy.
If you want to read more about this error from Microsoft, you can do so at this page:
http://support.microsoft.com/default.aspx?scid=kb;en-us;321915
 5:31 PM
5:31 PM
 File Under :
Informative
File Under :
Informative
We search for lots of information on the internet. But it is not necessary that others know about this. Whenever you visit any website this information is captured and stored in your computer in the form of 'cache', 'cookie', 'history', and 'windows registry'. There is a danger due to this. Whoever uses the same computer after you have used can find out which websites you have been visiting. If you have a personal computer that no one else will ever use, then you don't have to worry much about this. But if your home or office computer is shared then you better clear this history. In this tutorial let us see how to completely remove the recently visited websites from your computer.
1.Cache Folder
Every time you visit a website, every browser has the functionality to store the images, websites, urls etc in your hard disk somewhere in the temporary folders. This is useful to save bandwidth. When you visit the same website again, instead of downloading all the images again, the browser will retrieve them from the temporary folders from your hard disks and therefore increasing the speed and saving internet bandwidth. So when you finish browsing you can clear these temporary folders. This temporary folder is usually referred to as Cache. The exact location of this folder will differ based on the browser you are using. For instance if you use Internet explorer then this cache is located in the 'Temporary Internet Files' folder under your c:\Windows folder.
You can either delete from this folder or you can delete it from your browser. Goto Tools-> Internet Options. Under the General tab click 'Delete Files' button.
2.History
All the browsers also store the urls of every website you visit. This is used to show the address of the site on the 'Address Bar' when you start typing the first few letters of the websited address, the browser will take from the history and prompt you for the full address. This makes your job easier so that you need not type the full address every time. But if you want to hide the sites you visit then you have to remove this history also. Internet explorer stores this history in a folder called 'History' under c:\Windows folder.
Or you can delete history from your browser. Goto Tools-> Internet OPtions. Select the 'General' tab and click on 'Clear History' button. In the confirmation dialog box select 'OK'. This will clear your history.
3.Cookies
Whenever you visit websites, some information about you and some information about that website is stored in your computer's hard disk. When you visit the same site again, the information stored in this cookie file will be read to identify you. This is especially useful for sites that can personlize the site for you and displays messages such as 'welcome your_name' etc. But this cookie also stores the name of the site you visit so you should also delete these cookies if you want to hide the sites you visited.
To delete cookies, goto Tools->Internet Options. And click on 'Delete Cookies' button. Or you can choose the security tab and click on 'Custom Level' button to disable or enable cookies.
4. Registry
Another place in which the websites you visited are stored is the windows registry. It is not advisible to modify registries if you are not sure how to use them. Only those who are confident and willing to take risk should touch the registry. Click on 'Start->Run' and type 'regedit' and press enter. The windows registry will open. Now click on 'Edit->find' and type 'URL History'. In the right hand side you can see a list of website addresses that you visited. You can select them one by one and delete them. programs, viruses and hackers.
1.Cache Folder
Every time you visit a website, every browser has the functionality to store the images, websites, urls etc in your hard disk somewhere in the temporary folders. This is useful to save bandwidth. When you visit the same website again, instead of downloading all the images again, the browser will retrieve them from the temporary folders from your hard disks and therefore increasing the speed and saving internet bandwidth. So when you finish browsing you can clear these temporary folders. This temporary folder is usually referred to as Cache. The exact location of this folder will differ based on the browser you are using. For instance if you use Internet explorer then this cache is located in the 'Temporary Internet Files' folder under your c:\Windows folder.
You can either delete from this folder or you can delete it from your browser. Goto Tools-> Internet Options. Under the General tab click 'Delete Files' button.
2.History
All the browsers also store the urls of every website you visit. This is used to show the address of the site on the 'Address Bar' when you start typing the first few letters of the websited address, the browser will take from the history and prompt you for the full address. This makes your job easier so that you need not type the full address every time. But if you want to hide the sites you visit then you have to remove this history also. Internet explorer stores this history in a folder called 'History' under c:\Windows folder.
Or you can delete history from your browser. Goto Tools-> Internet OPtions. Select the 'General' tab and click on 'Clear History' button. In the confirmation dialog box select 'OK'. This will clear your history.
3.Cookies
Whenever you visit websites, some information about you and some information about that website is stored in your computer's hard disk. When you visit the same site again, the information stored in this cookie file will be read to identify you. This is especially useful for sites that can personlize the site for you and displays messages such as 'welcome your_name' etc. But this cookie also stores the name of the site you visit so you should also delete these cookies if you want to hide the sites you visited.
To delete cookies, goto Tools->Internet Options. And click on 'Delete Cookies' button. Or you can choose the security tab and click on 'Custom Level' button to disable or enable cookies.
4. Registry
Another place in which the websites you visited are stored is the windows registry. It is not advisible to modify registries if you are not sure how to use them. Only those who are confident and willing to take risk should touch the registry. Click on 'Start->Run' and type 'regedit' and press enter. The windows registry will open. Now click on 'Edit->find' and type 'URL History'. In the right hand side you can see a list of website addresses that you visited. You can select them one by one and delete them. programs, viruses and hackers.
 5:29 PM
5:29 PM
 File Under :
Informative
File Under :
Informative
If you are an Internet user, then you may have already used Google search engine. Google is not a mere search engine any more. Google provides many services free of charge to its users. In addition to being a search engine it provides many solutions and answers to many questions. One such value added service is the calculator in google.
You may have used your windows calculator from 'Accessories' for your calculations. This windows calculator can be used to solve simple arithmetic problems. In this calculator you can select 'View->Scientific' option to perform more complex operations such as log, sin, sum etc. But if you have questions such as 1 mile equals how many kilometers, 10 KG equals how many pounds or what is the celcius value of 18.6 Farenheit then, even this scientific calculator will not be of any help.
You can use google's calculator to answer these questions mentioned above as well as any other similar questions. Google's calculator can be used for simple, scientific calculations as well as for convertions.
Here are some examples and tips on how to use the google's calculator. First of all open the homepage of google. http://www.google.com . You can get the answers for your mathematical equations in the search box.
1. Type 3+4 in the search box and click on 'Search' button. Immediately you will see a calculator icon and the answer 3+4=7
2. +,-,/ and * keys represent addition, subtraction, division and multiplication respectively. For example you can key in 5+2*3 and click on search button to get the answer as 11.
3. You can also use the ^ key as the power symbol and the % symbol for percentage. If you type 2^10 then the answer will be 1024 which is number 2 multiplied ten times.
4. You can also use sqrt, sin, cos, tan, log, lm etc in google calculator search box. For example try the following log(200),sqrt(4),sin(45 degrees) etc.
5. You can also convert a number from one numbering format to another. Some of the the numbering formats are binary, decimal, octal and hexadecimal. As far as google is concerned binary is represented by 0b, octal is represented by 0o and hexa decimal is represented by 0x. If you remember these then you can easily convert from one format to another. You can test this using the following examples. 54 to binary, 123 to hex, 0b110010 to octal,0x789 to binary, 0x1234 in roman numerals.
6. You can also do conversions. For example, try the following phrases. 5 kilometers in miles, "2 miles in kilometers","100 degrees f in celcius", "One hour in seconds", "One decade in minutes".
You can get more details about google's calculator at http://www.google.com.sg/help/features.html#calculator
You may have used your windows calculator from 'Accessories' for your calculations. This windows calculator can be used to solve simple arithmetic problems. In this calculator you can select 'View->Scientific' option to perform more complex operations such as log, sin, sum etc. But if you have questions such as 1 mile equals how many kilometers, 10 KG equals how many pounds or what is the celcius value of 18.6 Farenheit then, even this scientific calculator will not be of any help.
You can use google's calculator to answer these questions mentioned above as well as any other similar questions. Google's calculator can be used for simple, scientific calculations as well as for convertions.
Here are some examples and tips on how to use the google's calculator. First of all open the homepage of google. http://www.google.com . You can get the answers for your mathematical equations in the search box.
1. Type 3+4 in the search box and click on 'Search' button. Immediately you will see a calculator icon and the answer 3+4=7
2. +,-,/ and * keys represent addition, subtraction, division and multiplication respectively. For example you can key in 5+2*3 and click on search button to get the answer as 11.
3. You can also use the ^ key as the power symbol and the % symbol for percentage. If you type 2^10 then the answer will be 1024 which is number 2 multiplied ten times.
4. You can also use sqrt, sin, cos, tan, log, lm etc in google calculator search box. For example try the following log(200),sqrt(4),sin(45 degrees) etc.
5. You can also convert a number from one numbering format to another. Some of the the numbering formats are binary, decimal, octal and hexadecimal. As far as google is concerned binary is represented by 0b, octal is represented by 0o and hexa decimal is represented by 0x. If you remember these then you can easily convert from one format to another. You can test this using the following examples. 54 to binary, 123 to hex, 0b110010 to octal,0x789 to binary, 0x1234 in roman numerals.
6. You can also do conversions. For example, try the following phrases. 5 kilometers in miles, "2 miles in kilometers","100 degrees f in celcius", "One hour in seconds", "One decade in minutes".
You can get more details about google's calculator at http://www.google.com.sg/help/features.html#calculator
Wednesday, September 24, 2008
 5:45 PM
5:45 PM
 File Under :
Informative
File Under :
Informative
Linux is an operating system that is now gaining popularity and competing against the Operating System giant, Microsoft. In 1993, a student in Finland, Linus Torralds, created Linux. Both home PCs as well as network Computers need an Operating System to function. Both home users and companies spend millions of dollars in purching these operating systems such as Microsoft Windows or Unix. How nice it will be if we can get a free Operating System. Well, Linux is a free open source Operating System that anybody, home user or companies can download and use it freely.
Linux is based on the Unix operating system. Linux solves all your needs. You can linux in a single computer or in a networked enviroment where there are thousands of computers.
But home users still have many doubts and questions about Linux. In this section we will see some of the frequently asked questions about linux.
There are many advertisements selling Linux. Isn't Linux Free?
Linux is totally FREE. You can download Linux from Internet. But if your internet connection is slow, then it may take several hours or even days to download linux and its related applications using your dial-up connection. Just calculate the phone charges and the internet connection charges for this time. If you have a high speed broadband then you will find no problem to download linux from the internet directly.
But to solve the issue for 'dial-up' users many companies download linux and copy it into CDs and sell them. The cost of the CD disk, the cost for sending the CD to your house, and for the service they provide, these companies may charge a meagre amount for the Linux CD. But if you directly download from Internet, it is totally free.
What is Redhat, SuSe?
These are names of companies that market and sell Linux. The heart of the Linux OS is its Kernel. These companies add many utilities and applications based on this kernel and sell it. There are many such companies such as RedHat, Mandrake, Debian, SuSe etc. The linux offered by these companies are called Linux Distributions or simply 'Distros'. The Kernel in all these Distros will be the same. But the utilities and applications may be different in different distros.
Can I copy the linux CD from my friend and install it in my computer?
By all means, Yes. You can make as many copies of the Linux CD of your friend. It is legal.
Is it very difficult to use Linux?
If you learn and know the linux commands then it is easy to operate your computer. The Character User Interface in Linux requires you to know and remember the commands. But using the 'Graphical User Interface' of Linux, anybody can use Linux without the need to learn and remember the commands. You can use desktop environments such as 'Gnome' or 'Kde' to get the graphical user interface. This GUI environment will be similar to the Windows environment.
Do all hardware work with Linux?
Some old hardware may not work with linux. But all the recent and new hardware works well in linux. A common hardware problem is with the 'winmodem'. If you are using this type of internal winmodem, then you may have to buy the latest modem.
Are there applications for Linux? Are they free?
There are plenty of applications for linux. Most of them are free. Open Office, GIMP, Real Player, MTV, Doom are some examples.
I do not want to stop using Windows. Can I still use Linux?
Yes you can. This is called Dual booting or Multibooting. You can install linux in a separate partition. Whenever you boot, you can select whether you want to boot from windows or linux.
Linux is based on the Unix operating system. Linux solves all your needs. You can linux in a single computer or in a networked enviroment where there are thousands of computers.
But home users still have many doubts and questions about Linux. In this section we will see some of the frequently asked questions about linux.
There are many advertisements selling Linux. Isn't Linux Free?
Linux is totally FREE. You can download Linux from Internet. But if your internet connection is slow, then it may take several hours or even days to download linux and its related applications using your dial-up connection. Just calculate the phone charges and the internet connection charges for this time. If you have a high speed broadband then you will find no problem to download linux from the internet directly.
But to solve the issue for 'dial-up' users many companies download linux and copy it into CDs and sell them. The cost of the CD disk, the cost for sending the CD to your house, and for the service they provide, these companies may charge a meagre amount for the Linux CD. But if you directly download from Internet, it is totally free.
What is Redhat, SuSe?
These are names of companies that market and sell Linux. The heart of the Linux OS is its Kernel. These companies add many utilities and applications based on this kernel and sell it. There are many such companies such as RedHat, Mandrake, Debian, SuSe etc. The linux offered by these companies are called Linux Distributions or simply 'Distros'. The Kernel in all these Distros will be the same. But the utilities and applications may be different in different distros.
Can I copy the linux CD from my friend and install it in my computer?
By all means, Yes. You can make as many copies of the Linux CD of your friend. It is legal.
Is it very difficult to use Linux?
If you learn and know the linux commands then it is easy to operate your computer. The Character User Interface in Linux requires you to know and remember the commands. But using the 'Graphical User Interface' of Linux, anybody can use Linux without the need to learn and remember the commands. You can use desktop environments such as 'Gnome' or 'Kde' to get the graphical user interface. This GUI environment will be similar to the Windows environment.
Do all hardware work with Linux?
Some old hardware may not work with linux. But all the recent and new hardware works well in linux. A common hardware problem is with the 'winmodem'. If you are using this type of internal winmodem, then you may have to buy the latest modem.
Are there applications for Linux? Are they free?
There are plenty of applications for linux. Most of them are free. Open Office, GIMP, Real Player, MTV, Doom are some examples.
I do not want to stop using Windows. Can I still use Linux?
Yes you can. This is called Dual booting or Multibooting. You can install linux in a separate partition. Whenever you boot, you can select whether you want to boot from windows or linux.
 5:44 PM
5:44 PM
 File Under :
Informative
File Under :
Informative
Internet has become part and parcel of our lives. Not only for individuals but even for a country's economic growth, scientific growth, organizations' success, Internet is very essential. The companies that offer these internet connections are called ISPs (Internet Service Providers). These ISPs offer many different internet connection plans. How to select the best connection plan for home use or for offices? The following tips will give you an overview of different types of internet connections, their advantages and disadvantages.
PSTN Dialup
Public Switched Telephone Network (PSTN) dialup uses your phone connection to connect your computer to the internet. You need a modem, phone line and a computer for a PSTN dial up connection.
Advantages of PSTN dial up
1. This is the basic internet connection and all the ISPs provide this type of dial up.
2. To install PSTN dialup and to use it is very cheap and affordable.
Disadvantages of PSTN dial up
1. The speed of a typical PSTN modem is 56KBPS. Therefore the speed of the internet connection will be slower than this.
2. During the time you are connected to the internet, you have to pay the telephone charges.
3. While you are connected to the internet you cannot use your telephone to call anyone because you are using that phone line for connecting to the internet. You also will not receive any calls from outside during this time.
ISDN dialup
Integrated Services Digital Network (ISDN) dialup uses a higher end digital telephone line to dial up. To use this type of connection you need ISDN telephone line, computer and a 'Terminal Adapter'.
Advantages of an ISDN dialup
1. While you are connected to internet using ISDN dialup connection you can use your ISDN phone to make phone calls simultaneously.
2. When you are making phone calls while connected to the internet then the speed of internet will be 64KBPS.
3. If you are using the ISDN phone line just for internet then the speed of internet will be 128KBPS.
Disadvantages of ISDN dialup
1. Not every place has ISDN connection.
2. Even if your place has this facility, it is expensive to get an ISDN dialup connection from your ISP.
3. Not all the ISPs provide ISDN dialup plan.
Leased Line Internet Plan
In both ISDN dialup and PSTN dialup you need to dial up from your computer before getting connected to the internet. And you close this connection when you no longer need internet connection. If you need a continuous connection 24 hours of the day and 7 days a week then you need a 'Leased Line' also known as 'dedicated line'. This type of permanent connection is called 'Always On'.
Advantages of Leased Line
1. You get 'Always on' connection 24 hours every day.
2. The speed of the internet ranges from 2.4 KBPS to 2G based on your subscription.
Disadvantages of Leased Line
1. The disadvantages of a leased line is that it is very expensive.
2. Since your computer is always connected to the internet your computer is exposed to many vulnerabilities such as viruses and spywares. So you may need to secure your computer using firewall and Antivirus software
DSL
1. Digital Subscriber Line (DSL) also uses a normal PSTN phone line. But using DSL you can use both internet and phone simultaneously. Therefore many prefer DSL to PSTN dial up.
Advantages of DSL
1. The speed of DSL connection is fast. 64 KBPS, 512 KBPS, 1.5MBPS and higher speed can be achieved in DSL connections.
2. DSL also provides 'Always On' connection 24 hours a day always.
3. You can also use your phone while using internet
Disadvantages of DSL
1. More expensive
2. You need an ADSL modem to connect but the distance between this modem and your computer cannot be more than 18,000 feet.
PSTN Dialup
Public Switched Telephone Network (PSTN) dialup uses your phone connection to connect your computer to the internet. You need a modem, phone line and a computer for a PSTN dial up connection.
Advantages of PSTN dial up
1. This is the basic internet connection and all the ISPs provide this type of dial up.
2. To install PSTN dialup and to use it is very cheap and affordable.
Disadvantages of PSTN dial up
1. The speed of a typical PSTN modem is 56KBPS. Therefore the speed of the internet connection will be slower than this.
2. During the time you are connected to the internet, you have to pay the telephone charges.
3. While you are connected to the internet you cannot use your telephone to call anyone because you are using that phone line for connecting to the internet. You also will not receive any calls from outside during this time.
ISDN dialup
Integrated Services Digital Network (ISDN) dialup uses a higher end digital telephone line to dial up. To use this type of connection you need ISDN telephone line, computer and a 'Terminal Adapter'.
Advantages of an ISDN dialup
1. While you are connected to internet using ISDN dialup connection you can use your ISDN phone to make phone calls simultaneously.
2. When you are making phone calls while connected to the internet then the speed of internet will be 64KBPS.
3. If you are using the ISDN phone line just for internet then the speed of internet will be 128KBPS.
Disadvantages of ISDN dialup
1. Not every place has ISDN connection.
2. Even if your place has this facility, it is expensive to get an ISDN dialup connection from your ISP.
3. Not all the ISPs provide ISDN dialup plan.
Leased Line Internet Plan
In both ISDN dialup and PSTN dialup you need to dial up from your computer before getting connected to the internet. And you close this connection when you no longer need internet connection. If you need a continuous connection 24 hours of the day and 7 days a week then you need a 'Leased Line' also known as 'dedicated line'. This type of permanent connection is called 'Always On'.
Advantages of Leased Line
1. You get 'Always on' connection 24 hours every day.
2. The speed of the internet ranges from 2.4 KBPS to 2G based on your subscription.
Disadvantages of Leased Line
1. The disadvantages of a leased line is that it is very expensive.
2. Since your computer is always connected to the internet your computer is exposed to many vulnerabilities such as viruses and spywares. So you may need to secure your computer using firewall and Antivirus software
DSL
1. Digital Subscriber Line (DSL) also uses a normal PSTN phone line. But using DSL you can use both internet and phone simultaneously. Therefore many prefer DSL to PSTN dial up.
Advantages of DSL
1. The speed of DSL connection is fast. 64 KBPS, 512 KBPS, 1.5MBPS and higher speed can be achieved in DSL connections.
2. DSL also provides 'Always On' connection 24 hours a day always.
3. You can also use your phone while using internet
Disadvantages of DSL
1. More expensive
2. You need an ADSL modem to connect but the distance between this modem and your computer cannot be more than 18,000 feet.
 5:43 PM
5:43 PM
 File Under :
Informative
File Under :
Informative
For one computer to connect to another computer and transfer information, the IP address of that computer should be known. This IP Address is made of numbers. The 32 Bit IP address is divided into 4 sections of 8 bits each separted by a '.' (dot). Each 8 bit is called an Octet. The value of each Octet will vary between 0 to 255.
For example, 203.116.56.34 is an IP address. As you can see there are four sections each separated by a dot.
Name Vs Number
If someone asks you whose phone number is 98343453 you may not know it. But instead if someone asks you whether you know 'John peters' immediately you will remember your friend. The reason is names are easier to remember than numbers. This is human nature.
In internet, there is a need to connect to a lot of different computers daily. If you have to remember the IP address of each computer in the internet, it is impossible. Because IP Address is made of numbers.
That's why, computer scientists decided to give a name to each of these IP addresses. These computer names that represent IP addresses are called 'Domain Names'. For example, www.yahoo.com is a domain name. It is easy to remember a name. Isn't it?
Every computer that connects to the internet has a unique IP Address. Most of the computers especially servers will have a domain name.
DNS - Domain Name System
If you need to connect to a computer in the internet, you can use the IP address of that computer or the Domain Name of that computer.
But the computers need just the IP addresses. For our own convenience we use domain names. Therefore when we use the domain name, for example www.yahoo.com, our computer will first find out the IP address of this domain name and then uses the IP address to connect to it.
Let us assume that the IP address of the computer that you want to connect to is 123.232.231.132 and the domain name of this computer is www.xyz.com .
Now you connect to Internet, open your browser and key in the IP address 123.232.231.132 in the address bar and 'Enter'. The browser will immediately connect to the computer because the computer knows how to use the IP address.
Now imagine that you typed the domain name www.xyz.com instead of the IP address in the browser. What the computer needs is the IP address not the domain name. Therefore the browser will try to find the IP address for the domain www.xyz.com . For this purpose it will contact the DNS (Domain Name System) server. The DNS server will find the IP address of that domain and will return the IP address to your browser. Then your computer will use that IP address to connect to that computer.
If you type the IP address, the browser will access that site immediately. If you type the domain name, there will be slight delay because the browser has to connect to DNS server first to determine the IP address. If for some reasons this DNS server is down or there is not DNS entry for that domain, then that domain name or website address will not be accessible.
For example, 203.116.56.34 is an IP address. As you can see there are four sections each separated by a dot.
Name Vs Number
If someone asks you whose phone number is 98343453 you may not know it. But instead if someone asks you whether you know 'John peters' immediately you will remember your friend. The reason is names are easier to remember than numbers. This is human nature.
In internet, there is a need to connect to a lot of different computers daily. If you have to remember the IP address of each computer in the internet, it is impossible. Because IP Address is made of numbers.
That's why, computer scientists decided to give a name to each of these IP addresses. These computer names that represent IP addresses are called 'Domain Names'. For example, www.yahoo.com is a domain name. It is easy to remember a name. Isn't it?
Every computer that connects to the internet has a unique IP Address. Most of the computers especially servers will have a domain name.
DNS - Domain Name System
If you need to connect to a computer in the internet, you can use the IP address of that computer or the Domain Name of that computer.
But the computers need just the IP addresses. For our own convenience we use domain names. Therefore when we use the domain name, for example www.yahoo.com, our computer will first find out the IP address of this domain name and then uses the IP address to connect to it.
Let us assume that the IP address of the computer that you want to connect to is 123.232.231.132 and the domain name of this computer is www.xyz.com .
Now you connect to Internet, open your browser and key in the IP address 123.232.231.132 in the address bar and 'Enter'. The browser will immediately connect to the computer because the computer knows how to use the IP address.
Now imagine that you typed the domain name www.xyz.com instead of the IP address in the browser. What the computer needs is the IP address not the domain name. Therefore the browser will try to find the IP address for the domain www.xyz.com . For this purpose it will contact the DNS (Domain Name System) server. The DNS server will find the IP address of that domain and will return the IP address to your browser. Then your computer will use that IP address to connect to that computer.
If you type the IP address, the browser will access that site immediately. If you type the domain name, there will be slight delay because the browser has to connect to DNS server first to determine the IP address. If for some reasons this DNS server is down or there is not DNS entry for that domain, then that domain name or website address will not be accessible.
Tuesday, September 23, 2008
 5:49 PM
5:49 PM
 File Under :
Informative
File Under :
Informative
In 1980s there was a tussle between VHS and Betamax technologies. VHS (Victor Home System) and Sony's Betmax were two different standards in Video tapes. People were confused as to which video tape to choose. Twenty five years later now there is a similar comparison in DVD technologies. They are DVD+R and DVD-R.
The use of DVD writers is increasing tremendously. If you are thinking of buying a DVD writer, you can read buying tips on DVD writers. Though the DVD disks are same, the DVD burning methods differ. Among these two technologies DVD+R is a more advanced technology. That is why these DVD+R disks are expensive compared to DVD-R. DVD-R is a comparitively older technology.
Now the next issue is your DVD burning software. Some buy DVD burning software without checking whether that DVD burning software supports both DVD+R and DVD-R disks. So though it is a bit more expensive get a software that supports both DVD+R and DVD-R technologies.
The use of DVD writers is increasing tremendously. If you are thinking of buying a DVD writer, you can read buying tips on DVD writers. Though the DVD disks are same, the DVD burning methods differ. Among these two technologies DVD+R is a more advanced technology. That is why these DVD+R disks are expensive compared to DVD-R. DVD-R is a comparitively older technology.
Now the next issue is your DVD burning software. Some buy DVD burning software without checking whether that DVD burning software supports both DVD+R and DVD-R disks. So though it is a bit more expensive get a software that supports both DVD+R and DVD-R technologies.
 5:48 PM
5:48 PM
 File Under :
Tips And Tricks
File Under :
Tips And Tricks
In most places, many people use the same computer. Especially in a home, many family members use the same computer. In such a scenario, the emails sent to one person can be easily read by other persons using the same computer. In such cases, is it possible to create individual inboxes for each member and secure it with a password, so that each one can access only their email inbox.
Yes, it is possible. MS Outlook makes it possible for you. In MS Outlook you can create your own message folders, contacts for each one separately. You can create these for each individual users and make it secure by protecting these folders with password so that each person can see only their folder. Just follow these steps to protect your email inbox with password.
1. First of all you need to create a new Identity. Select 'File->Identities->Add New Identity' option. Here you create a new user with a 'user name'. Also select the 'Require a password' option and key in the 'password'. Remember this username and password for future use.
2. Now, it will prompt and ask whether you want to register this new user and log in, click on 'Yes' and enter all your personal details in the following screen. Now you have created yourself as the new user and you have protected your inbox with your password.
3. Likewise, you can create identities for each member of the family.
4. After creating many identities, each user can see their protected inbox by choosing 'File->Switch identities' and key in their username and password to see their inbox.
Similarly Netscape Mail version 7 has this multi user feature. But it is not protected using password.
If you use web mails such as yahoo, gmail or hotmail then you do not have to worry, since you can only view your emails by logging in each time.
Yes, it is possible. MS Outlook makes it possible for you. In MS Outlook you can create your own message folders, contacts for each one separately. You can create these for each individual users and make it secure by protecting these folders with password so that each person can see only their folder. Just follow these steps to protect your email inbox with password.
1. First of all you need to create a new Identity. Select 'File->Identities->Add New Identity' option. Here you create a new user with a 'user name'. Also select the 'Require a password' option and key in the 'password'. Remember this username and password for future use.
2. Now, it will prompt and ask whether you want to register this new user and log in, click on 'Yes' and enter all your personal details in the following screen. Now you have created yourself as the new user and you have protected your inbox with your password.
3. Likewise, you can create identities for each member of the family.
4. After creating many identities, each user can see their protected inbox by choosing 'File->Switch identities' and key in their username and password to see their inbox.
Similarly Netscape Mail version 7 has this multi user feature. But it is not protected using password.
If you use web mails such as yahoo, gmail or hotmail then you do not have to worry, since you can only view your emails by logging in each time.
 5:47 PM
5:47 PM
 File Under :
Tips And Tricks
File Under :
Tips And Tricks
There is always a danger that your emails are snatched on their way and be read. Luckily there are ways that you can use to make these emails unreadable by others on the way. In this article we shall see methods to secure your emails by encrypting them.
Assume that Jack is sending an email to Stella. This email can be read by anyone who has access to this email on the way. If Jack wants that no one else other than Stella should be able to read this email then what can he do? Here's where public key and private key can come to the rescue.
What is public Key and Private Key?
Here KEY is referred to the string made of 0s and 1s. There are 64bit, 128bit and 256bit keys. A 64bit key means that it contains a combination of 64 0s and 1s.
If the number of bits in a key is more then it is more difficult to crack it. Each one has to create a public key and a private key and inform other s about the public key. The private key should not be revealed to anyone else.
A readable text is called 'clear text' or 'plain text'. To make this message unreadable you have to encrypt it using your public key or the private key. This encrypted text is then called 'cyber text'. So 'clear text' is encrypted to make a 'cyber text'.
To convert the encrypted text back to its readable form is called 'decryption'. In order to decrypt you should use one's public key or the private key. It should be noted that a message that was encrypted using public key can only be decrypted using its private key. And the message that was encrypted using the private key has to be decrypted using its corresponding public key. So a person's public key and private keys are pairs and has to be used in pair.
How will we know the public key of someone?
We can send our public key to others through email. Or you may want to publish it in your personal website for your friends to see. You may even print your public key in your name card. You can also publish your public key in a 'Public Key Directory'.
To confirm the recipient of the email.
Let us go back to the same example. When Jack composes an email he will use the public key of Stella to encrypt the message. Then he will send this cyber text(encrypted email) via internet to Stella. If someone gets this message in between he cannot read this message as it is encrypted. The reason is because the message is encrypted using Stella's public key. So this message is readable only if it is decrypted. To decrypt this message Stella's Private key is required. Only Stella knows her private key. So others cannot read this message.
In this method the recipient is confirmed because only Stella can read this message. But how to find that this message is from Jack and not anybody else. To confirm the sender follow the method as described below.
To confirm the Sender
If Jack creates an email and encrypts the message using his private key and encrypts the message and sends it to Stella. So whoever knows Jack's public key can decrypt this message and read it.
By this method the sender of the message is confirmed as Jack. But not only Stella, any others who knows jack's public key can decrypt the message. In this method therefore the recipient is not secured only the sender is confirmed.
To secure both the sender and recipient.
In both the methods discussed above the message is encrypted only once. If instead the message is encrypted twice then both the sender and recipient can be confirmed.
So to achieve this, Jack should encrypt the message using his Private key first. After that he has to encrypt again using Stella's Public Key and then send it to Stella.
By this method only Stella can decrypt the message fully and read it
Assume that Jack is sending an email to Stella. This email can be read by anyone who has access to this email on the way. If Jack wants that no one else other than Stella should be able to read this email then what can he do? Here's where public key and private key can come to the rescue.
What is public Key and Private Key?
Here KEY is referred to the string made of 0s and 1s. There are 64bit, 128bit and 256bit keys. A 64bit key means that it contains a combination of 64 0s and 1s.
If the number of bits in a key is more then it is more difficult to crack it. Each one has to create a public key and a private key and inform other s about the public key. The private key should not be revealed to anyone else.
A readable text is called 'clear text' or 'plain text'. To make this message unreadable you have to encrypt it using your public key or the private key. This encrypted text is then called 'cyber text'. So 'clear text' is encrypted to make a 'cyber text'.
To convert the encrypted text back to its readable form is called 'decryption'. In order to decrypt you should use one's public key or the private key. It should be noted that a message that was encrypted using public key can only be decrypted using its private key. And the message that was encrypted using the private key has to be decrypted using its corresponding public key. So a person's public key and private keys are pairs and has to be used in pair.
How will we know the public key of someone?
We can send our public key to others through email. Or you may want to publish it in your personal website for your friends to see. You may even print your public key in your name card. You can also publish your public key in a 'Public Key Directory'.
To confirm the recipient of the email.
Let us go back to the same example. When Jack composes an email he will use the public key of Stella to encrypt the message. Then he will send this cyber text(encrypted email) via internet to Stella. If someone gets this message in between he cannot read this message as it is encrypted. The reason is because the message is encrypted using Stella's public key. So this message is readable only if it is decrypted. To decrypt this message Stella's Private key is required. Only Stella knows her private key. So others cannot read this message.
In this method the recipient is confirmed because only Stella can read this message. But how to find that this message is from Jack and not anybody else. To confirm the sender follow the method as described below.
To confirm the Sender
If Jack creates an email and encrypts the message using his private key and encrypts the message and sends it to Stella. So whoever knows Jack's public key can decrypt this message and read it.
By this method the sender of the message is confirmed as Jack. But not only Stella, any others who knows jack's public key can decrypt the message. In this method therefore the recipient is not secured only the sender is confirmed.
To secure both the sender and recipient.
In both the methods discussed above the message is encrypted only once. If instead the message is encrypted twice then both the sender and recipient can be confirmed.
So to achieve this, Jack should encrypt the message using his Private key first. After that he has to encrypt again using Stella's Public Key and then send it to Stella.
By this method only Stella can decrypt the message fully and read it
Monday, September 22, 2008
 5:44 PM
5:44 PM
 File Under :
Hardware And Networking,
Tips And Tricks
File Under :
Hardware And Networking,
Tips And Tricks
Some readers says that while is inserting flash drive in USB port. The system didn’t recognize it how could we overcome it.
First of all we should know the two types of USB ports.
USB 1.1: This is the first type of USB. It designed as per the speed of transferring 1.5mb/sec data’s. This is designed instead of serial and parallel port for the use of USB port. This is basically used only for connecting mouse and keyboard. System would be struggled for data overloading.
USB 2.0: This kind of USB ports is used for large scale into data transfer. More readers ask that how to identify these two kind of USB ports. To identify the model use the following commands. Start=>My computer=> properties. And click Hardware tab after than select Device Manager. Now you got the list. In that list select the plus symbol that is located after “Universal Serial Bus controllers” if your system have USB 1.1 mean it displays as “Host controller (or) Open Host Controller”. Else USB 2.0 is used mean it displays like.” Enhanced host controller (or) USB 2.0 controller.
Your windows operating system says that the connected USB get speeded. When you are connecting the high speed USB to logo speed USB port of the system, but most of the reader saying that while connecting the USB device to the system. The device was not getting detected. Commonly while inserting an USB device to the system. Window XP will say new hardware found. This message will display in the hard disk. While inserting the USB device it will get auto play, and enquire whether to open the files as file (Or) audio format (Or) video format? It assigns a drive letter for it. If all the details mentioned above had not displayed means the inserted device had not matched with your operating system. You can solve this by doing below.
Go to Start => control panel =>Administrative Tools and click in administrative tool. After that double click on Computer Management.
In that left side select Disk Management, at the right side a drive displays with the name of a removable drive. This is the drive thus containing to same name of already using drive.
To change it right click on the while bar then a got a list.
Now select “change drive letters and paths”.
Now you can select the letter that you want. Click the “change” option.
The letter that you selected it should be already used one.
After finishing this you should get a warning message.
Now click ok to it.
Now close the computer management console while clicking the My computer icon.
You can see the USB drive’s letter.
We face more problems on problem on using USB port. Some part may become in accessible due to the power shortage of computer. These kinds of problems happen on USB 1.1 ports only. These problems happen only on windows 2000 and the before edition while getting these kind of problems. We just disconnect the instruments after that connect one by one.
Now a days the new version computer consists of at-least four USB ports. Two ports are fixed in backside and the remaining two parts are fixed in front side. Windows XP packages will manage these ports without any problems.
First of all we should know the two types of USB ports.
USB 1.1: This is the first type of USB. It designed as per the speed of transferring 1.5mb/sec data’s. This is designed instead of serial and parallel port for the use of USB port. This is basically used only for connecting mouse and keyboard. System would be struggled for data overloading.
USB 2.0: This kind of USB ports is used for large scale into data transfer. More readers ask that how to identify these two kind of USB ports. To identify the model use the following commands. Start=>My computer=> properties. And click Hardware tab after than select Device Manager. Now you got the list. In that list select the plus symbol that is located after “Universal Serial Bus controllers” if your system have USB 1.1 mean it displays as “Host controller (or) Open Host Controller”. Else USB 2.0 is used mean it displays like.” Enhanced host controller (or) USB 2.0 controller.
Your windows operating system says that the connected USB get speeded. When you are connecting the high speed USB to logo speed USB port of the system, but most of the reader saying that while connecting the USB device to the system. The device was not getting detected. Commonly while inserting an USB device to the system. Window XP will say new hardware found. This message will display in the hard disk. While inserting the USB device it will get auto play, and enquire whether to open the files as file (Or) audio format (Or) video format? It assigns a drive letter for it. If all the details mentioned above had not displayed means the inserted device had not matched with your operating system. You can solve this by doing below.
Go to Start => control panel =>Administrative Tools and click in administrative tool. After that double click on Computer Management.
In that left side select Disk Management, at the right side a drive displays with the name of a removable drive. This is the drive thus containing to same name of already using drive.
To change it right click on the while bar then a got a list.
Now select “change drive letters and paths”.
Now you can select the letter that you want. Click the “change” option.
The letter that you selected it should be already used one.
After finishing this you should get a warning message.
Now click ok to it.
Now close the computer management console while clicking the My computer icon.
You can see the USB drive’s letter.
We face more problems on problem on using USB port. Some part may become in accessible due to the power shortage of computer. These kinds of problems happen on USB 1.1 ports only. These problems happen only on windows 2000 and the before edition while getting these kind of problems. We just disconnect the instruments after that connect one by one.
Now a days the new version computer consists of at-least four USB ports. Two ports are fixed in backside and the remaining two parts are fixed in front side. Windows XP packages will manage these ports without any problems.
 5:44 PM
5:44 PM
 File Under :
Tips And Tricks
File Under :
Tips And Tricks
We can print one document in Windows XP. But how to we print all files in the folders? Ok. If one folder has 10 files we can open all files and then give print command. If 100 files are there and you have to take a printout of all of them what can we do? Here only notepad comes to our help here we can write a batch file and command it to print from a right place. Lets see briefly how is this done.
First of all open note pad, through Start, All Programs, Accessories, Notepad then type the following code without fault.
@echo off
dir%1/-p/o: gin>
“%temp%\listing”
Start/wnotepad/p”%temp%\listing”
Del”%temp%%\listing”
exit
Save the file as printdir.bat, then save it in c:\windows folder. A small tip: - you can save this file in any name but you must give the extension as .bat only. Now you have successfully created a file to print. Now, let’s see how to print all files in a folder,
1) First double click the My Computer icon.
2) Select Folder options from the Tools menu
3) Then Click File types tab, it will be in the upper side of the screen.
4) You will find a file type below” Registered file types”
5) Select it and click Advanced Tab
6) This opens Edit File Type. In this you can see a button “New” click it
7) New action dialog box opens
8)Type print directory in action tab
9) Browse for c:\windows\printdir.bat through browse button at application used to perform action
10) Click ok and close all the dialog boxes
If lot of files is to be printed we can create a folder and put them inside it, now right click on the folder and select print directory option in it, if you select this all files in the folder will be printed.
First of all open note pad, through Start, All Programs, Accessories, Notepad then type the following code without fault.
@echo off
dir%1/-p/o: gin>
“%temp%\listing”
Start/wnotepad/p”%temp%\listing”
Del”%temp%%\listing”
exit
Save the file as printdir.bat, then save it in c:\windows folder. A small tip: - you can save this file in any name but you must give the extension as .bat only. Now you have successfully created a file to print. Now, let’s see how to print all files in a folder,
1) First double click the My Computer icon.
2) Select Folder options from the Tools menu
3) Then Click File types tab, it will be in the upper side of the screen.
4) You will find a file type below” Registered file types”
5) Select it and click Advanced Tab
6) This opens Edit File Type. In this you can see a button “New” click it
7) New action dialog box opens
8)Type print directory in action tab
9) Browse for c:\windows\printdir.bat through browse button at application used to perform action
10) Click ok and close all the dialog boxes
If lot of files is to be printed we can create a folder and put them inside it, now right click on the folder and select print directory option in it, if you select this all files in the folder will be printed.
 5:44 PM
5:44 PM
 File Under :
Tips And Tricks
File Under :
Tips And Tricks
To get † symbol use Alt+0134
To get ‡ symbol use Alt+0135
To create the trade mark (™) symbol use Alt+0153
To get bound sterling (£) symbol use Alt+0163
To get the Japanese currency yen (¥) symbol use Alt+0165
To get copy right symbol (©) use Alt+0169
To get registered trade mark symbol (®) use Alt+0174
To get degree symbol (°) use Alt+0176
To show (±) symbol use Alt+0177
To show super script 2 symbol (²) use Alt+0178
To show super script 3 symbol (³) use Alt+0179
To make a center dot symbol (•) use Alt+0183
To describe ¼ use Alt+0188
To describe ½ use Alt+0189
To describe ¾ use Alt+0190
We can create more symbols as same as above. We mostly use the above symbols. To see more combinations of symbols visit at http://home.earthlink.net/~awinkelried/keyboard_shortcuts.html
To get ‡ symbol use Alt+0135
To create the trade mark (™) symbol use Alt+0153
To get bound sterling (£) symbol use Alt+0163
To get the Japanese currency yen (¥) symbol use Alt+0165
To get copy right symbol (©) use Alt+0169
To get registered trade mark symbol (®) use Alt+0174
To get degree symbol (°) use Alt+0176
To show (±) symbol use Alt+0177
To show super script 2 symbol (²) use Alt+0178
To show super script 3 symbol (³) use Alt+0179
To make a center dot symbol (•) use Alt+0183
To describe ¼ use Alt+0188
To describe ½ use Alt+0189
To describe ¾ use Alt+0190
We can create more symbols as same as above. We mostly use the above symbols. To see more combinations of symbols visit at http://home.earthlink.net/~awinkelried/keyboard_shortcuts.html
Sunday, September 21, 2008

HOLLYWOOD - Pop singer George Michael has been arrested after police caught him in possession of drugs.
The Careless Whisper hitmaker was detained on Friday, September 19, in the Hampstead Heath area of north London, close to his home in Highgate.
The singer was questioned at a nearby police station and later released with a caution for possessing class A and class C drugs--cocaine and cannabis.
A spokesman for the Metropolitan Police says, "We can confirm a 45-year-old man was arrested in the Hampstead heath area on the 19th September on suspicion of possessing drugs saying:
"He was taken to a North London police station where he received a caution and was released with no further action. The caution was for the possession of class A and class C drugs, cocaine and cannabis."
Michael was previously arrested in October 2006 in London, when cops found him slumped over the wheel of his car. And last May he was handed a
two-year driving ban after pleading guilty to driving while unfit through drugs.

LG 60″ Plasma 1080p HDTV Introduction
Don’t just watch it, Live it. In LG Full HD!
The LG 60PY3D features a full HD Resolution Displays that shows programs in full 1920 x 1080p resolution for a more detailed picture. High-definition Television (HDTV) makes any room in your home come alive.
LG 60″ Plasma 1080p HDTV Design
Aspect Ratio 16:9
Contrast Ratio 3,000:1
Resolution 1920 x 1080
Dimensions w/Out Stand (W x H x D) 63.5″ x 37.8″ x 4.6″
Weight w/Out Stand 142.4 lbs.
Dimensions w/Stand (W x H x D) 63.5″ x 40.4″ x 18″
Weight w/Stand 177.7 lbs.
Dimensions w/Packaging (W x H x D) 69.3″ x 45.1″ x 21.6″
Weight In Package 199.7 lbs.
LG 60″ Plasma 1080p HDTV Features
60″ Full HD Plasma Television
Full HD 1920 x 1080p Native Resolution
ATSC/NTSC Tuners, XD Engine
16-bit Colour Processing
PC Input, 3 HDMI Input
XD Engine
LG SimpLink
LG 60″ Plasma 1080p HDTV Performance
Known as Full High Definition, 1080p displays are capable of showing every single pixel of the highest-resolution HD content, DVD’s and video games. 1080p resolution is about twice the resolution of 1080i HDTVs, and delivers a quality of detail and realism other TVs simply can’t touch. This plasma HDTV features LG’s XD Engine that takes the resolution of analog signals to near-HD levels by improving brightness, contrast, detail and enhancing color as well as reducing signal noise. A liquid plasma display can recreate more realistic black-levels than an LCD display can.
What’s included in the package
60″ flat-panel plasma HDTV, TV stand and Remote.
Conclusion
LG’s innovations result in cinema-like high resolution images. With built-in HDTV compatibility, this TV set can display images that are significantly sharper and more realistic than regular television.

Microsoft's new lower prices for its Xbox 360 family of consoles in Europe have gone into effect today.
With a new low entry-level price of £129.99, we were interested to know if this would tip Pocket-lint readers into taking the Xbox plunge.
In our latest reader poll, we asked "Does the Xbox 360 price cut tempt you to buy?"
It seems the low pricing has just about won you over with 52% saying yes and 48% answering no.
Microsoft now describes the Xbox 360 as "the true home of mass market entertainment with something to offer for every interest and budget".
As from today, the new prices are £129.99 for the Xbox 360 Arcade console, the standard model with 60GB hard drive and one wireless controller will set gamers back £169.99.
The top-of-the-line Xbox 360 Elite, which comes with a 120GB hard drive is on sale for £229.99.

Gadgets designed by those who are aimed to make life easier and more interesting for disabled people, sometimes unveil new course for hi-tech industries. The most recent gadget that stands at origin of computing devices for disabled is a latest concept cursor manipulator. This light detector attached to one’s spectacles can act as good as a well-known computer mouse and was designed to substitute it completely. The Wink Technology which is in its core can also be, by the way, very handy to all computer users, probably even entice them all.

Jedlicka Institute for Disabled Children, Czech Republic, has become a domain for the gadget’s developers. To make a computer controllable for handicapped persons, researchers and students of this institute have placed a camera locked close to user’s eye. It is programmed to detect eye’s behavior – left, right, up and down movements, and moments when the eye is closed for calculated periods of time. This was the hardest thing to do as the involved students and other researchers say. The device can not only be eye-controlled, but can also perceive head movements. Data from the detector is sent to a control unit and generated into orders computer will understand. Overall cursor on the monitor receives all the commands and follows the way eyeball shows. Shortly closed eye is interpreted as a click, and prolonged eye closing means a double click for eye-controlled computer. Now gadget is completely useable, makes all the computer and Internet resources manageable and is compatible with any PC model. Device is synchronized via USB host.
Wink Technology is unfortunately not the cheapest one. This eye-controlled cursor manipulator will cost slightly more than 1500 Euros but it was said that government and charitable foundations are willing to cover at least a part of the price for disabled children, because it finally offers them Internet resources and computer experience, which means better education and profitable employment.
Friday, September 19, 2008

Four laptop computers have been stolen from the government agency that oversees bankrupt companies, officials said Wednesday, in the latest security breach involving digitally stored data belonging to the British government. The agency, the Insolvency Service, said that one of the laptops contained personal information about former directors of 122 bankrupt companies.

Teknocreations’ InCharge charging system charges wiimotes without opening the battery cover. Let me emphasize that again: it charges the wiimote through the battery cover AND the wiimote jacket. Hallelujah!
Swapping batteries on a dressed up wiimote, and frequently mind you, is an exercise in pure frustration (absolute evil, don’t try it at home, kids). By the time the batteries are replaced, one has an irresistable urge to chuck it at the TV and cackle like a madman which, pretty much, defeats the purpose of the grip cover.
Now, all you’ve got to do is put it in the cradle, so very gently, and let the power flow into the lithium polymer battery pack. Kinda like an electric toothbrush.

I’m a pretty devout iPhone user. My original iPhone has been good to me. The new 2.0 firmware upgrade takes the device to a whole new level of awesomeness. But as awesome as the iPhone is, I couldn’t help but drool a bit when I first glimpsed the BlackBerry Bold. RIM promised a unique mix of form and function and according to the Boy Genius Report, they’ve pretty much delivered.
Boy Genius had a chance to take the Bold on a month long field test (seriously, we’re jealous) and the results are pretty much what most of us expected. It’s exactly what BlackBerry fans have been waiting for. Boy Genius says it best when they refer to the Bold as the “BlackBerry communities iPhone”.

The Sansa Fuze from SanDisk, is a cool little MP3/4 player along the same vein as the iPod Nano. We’ve recently been sent one to play with so here are our thoughts and findings (or a review so to speak).
Aesthetically the Fuze is a cute little player.The physical UI consists of a rotating front dial which also acts as the 4 navigation buttons with the center button for selection. The display crisp with a resolution of 220 x 176, large enough for watching the odd music video but you wouldn’t want to watch a feature length film on it. Sound quality was good (though as with just about any MP3 player the supplied headphones aren’t the greatest). What most impressed me about the Fuze are the extra features that you don’t find on other (note iPod) players, including:
* Built in microphone
* FM radio
* microSD Slot, a really cheap way to expand the capacity
* Easy to transfer files (drag and drop) without the need of propriety software
Though there are a few downsides:
* Propriety USB connection, it obviously comes the cable but a standard mini USB connection would be much more convenient especially for charging
* You bookmark videos but not audio books
*
The Fuze comes in 2, 4 and 8GB versions with prices starting from ~$70 at Amazon.
Thursday, September 18, 2008

If a few months ago Sony-Ericsson announced launching of XPERIA X1 that included a lot of functions (wireless data transfers, photo camera, media player, 3D games, aGPS etc.) by launching of C905 company offers to the clients the first Cyber-shot slide-to-open mobile phone which incorporates a 8,1 mega-pixels camera, 16x digital zoom, xenon flash.
It can catch video sequences and includes some technologies known to the users of digital cameras as: image stabilization, auto focus, an intelligent regulation of contrast and face detection. It is also equipped with 2 GB Memory Stick Micro card, USB adaptor (CCR-70) and 2.4 inches screen that is resistant to scratches. The images can be viewed on a TV set via WiFi or a cable, or can be sent to another gadget by Bluetooth.
C905 Cyber-shot was launched in 3 versions: C905, C905a and C905c and will be available in 3 colors: Night Black, Ice Silver and Copper Gold. The phone can be used for supporting video-conferences, can perform functions of a media player, FM radio and aGPS. It supports the following connections: GSM, GPRS and EDGE and first two models also support UMTS and HSDPA connections. You can also access e-mail and can navigate through the internet with this gadget.
On the market this model is expected by the end of 2008, but the company hasn’t announced any price yet.
 5:44 PM
5:44 PM
 File Under :
Hardware And Networking
File Under :
Hardware And Networking

AMD redefines with Radeon 4670 and Radeon 4650 what means mainstream graphic plaques.
AMD fulfill their promises and launches officially a new series of graphic plaques - ATI Radeon HD 4600 that intend to offer an exceptional performance for games and HD multimedia, at power consumption lower than one of a bulb. And all these at a very attractive price for graphic plaques from mainstream category.
4600 graphic plaque series are practically limited versions of 4800 series, with what AMD succeeded to overcome those from Nvidia. They are based on TeraScale graphic processor, realized in 55 nm and with 320 stream processors that is a modified RV770.
ATI Radeon HD 4670 works at a 750 MHz nuclear frequency, 2 GHz memory frequency, has a memory interface on 256 bits, and can include 512 MB or 1 GB of GDDR3 memory.
Less powerful version, ATI Radeon HD 4650, has a 600MHz nuclear frequency, 1GHz memory frequency, memory interface on 128 bits and includes 512 MB of GDDR2 memory.
Both of these plaques have 320 stream processors, 32 texture units and support DirectX 10.1, include Unified Video Decoder (UVD) 2.0 for HD video processing and HDMI 7.1 surround sound audio.
Plaques have a reduce power consumption, 60 W for 4670 and 50 W for 4650. Prices are extremely attractive, being smaller than initial estimations. So, HD 4670 with 512 MB of memory costs 80 dollars (version with 1 GB will appear later), and HD 4650 has a price of 60 dollars.
From initial reviews performance of these gadgets seems to be excellent, considering low power consumption and price. So HD 4670 is situated somewhere among Radeon HD 3650 or GeForce 9500 GT and Radeon HD 3850 or GeForce 9600 GT/GSO in some tests even overcoming them.

It seems that ASUS has some aces in sleeve when it is time to talk about touchscreen terminals and it is not only the P552W model but also a new handset Asus Galaxy7.
The Asian company is planning to launch a terminal that will be a rival for Samsung Omnia and that includes a touchscreen (WQVGA or WVGA) plus a 5 MP camera, a trackball for a non-touch navigation and 3G connectivity and WiFi. The list of specifications is ending yet here, but speculations continue till we wait an official announce from the ASUS.
We hope that the new handset will be at least the same competitive as others recently launched Windows Mobile terminals especially in memory capacity and processor performance. If we talk about the interface we hope that ASUS will be a viable alternative that will perfectly suite to Windows Mobile 6.1 OS.

you are a MacBook Air owner who needs extra storage for your important data, then you should buy the Iomega’s latest eGo external USB hard drive. This storage device is specially built for MacBook Air and offers 320GB storage. The external hard driv comes in an aluminum chassis. The Iomega eGo Hard Drive retails for $150 each. [Boing Boing]

The pricing detail of the spanking new Raon Digital’s Everun Note has been unveiled. Priced at $879 upwards, the netbook comes with several cool specs including 7 inch touchscreen display(1,024 x 600 resolution), an AMD Turon 64×2 Dual Core 1.2GHz processor, 4-mode rotation, dual monitor support, and an optical nub for easy navigation. Its battery provides up to 2.5 hours of battery life for a normal use. [Dynamism via Laptop Notebook News]

The Elements Stardust is a crystal-studded radio that can be a perfect gift for your geek girlfriend. It is actually a Sonoro musical player that has been covered with 3,900 Swarovski crystals in a white floral pattern with a background of black crystals. It was unveiled at the IFA 2008 in Berlin. Other features include 10 preset AM/FM stations, iPod/notebook/PMP compatibility, and an integrated alarm clock. [BornRich]
Subscribe to:
Comments (Atom)

Search By Google
Followers
Labels
- 3G (1)
- Adsense (3)
- Amd (1)
- Applications (2)
- Articles (1)
- AT and T (1)
- Automobile (2)
- Blog (8)
- Blogger (8)
- Bluetooth (4)
- Broadband (3)
- Camera (3)
- CdInformative (1)
- Certification (1)
- Cookies (1)
- Data Cable (1)
- Desktop (1)
- Displays (1)
- Download (1)
- Earn Money (1)
- Educational (55)
- Facebook (2)
- Faqs (11)
- Fax (1)
- Fiber Optic (1)
- Fixing Problem (1)
- Folder (1)
- Gadgets (203)
- Gaming (1)
- Gmail (2)
- Google (4)
- Gps (1)
- Hard Disk (2)
- Hardware And Networking (13)
- Hd (3)
- Headphones (1)
- Help (2)
- Hotmail (1)
- Ideas (1)
- Informative (196)
- Infrared (1)
- Intel (2)
- Internet (57)
- iPhone (3)
- iPods (1)
- IT (3)
- KeyBoard (2)
- Lan (1)
- Laptops (7)
- Lcd (2)
- Led (1)
- Marketing (2)
- Markets (1)
- Media Players (1)
- Microsoft (7)
- Mobiles (44)
- MobilesTech (1)
- Modem (1)
- MotherBoard (2)
- Motorola (1)
- Movies (1)
- Mp3 (2)
- Ms Dos (1)
- News (79)
- Nitendo (1)
- Nokia (3)
- Notebook (1)
- Notepad (1)
- Others (1)
- Piracy (1)
- Portable (1)
- Presentations (1)
- Remote (1)
- Reports (1)
- Researches (2)
- Reviews (47)
- School (7)
- Search (2)
- Security (4)
- Seo (3)
- Shortcut (1)
- Sms (1)
- Software (2)
- Spyware (1)
- Surveys (2)
- Symbian (1)
- System (2)
- T-Mobile (1)
- Tech (7)
- Tips And Tricks (119)
- Tools (1)
- Traffic (1)
- Universities (2)
- Usb (4)
- Video (2)
- ViewSonic (1)
- Viruses (1)
- Web Designing (1)
- Website (1)
- Wifi (1)
- Win 2000 (1)
- Win 95 (1)
- Win 98 (1)
- Win Me (1)
- Win NT (1)
- Win Vista (4)
- Windows (22)
- Windows 7 (2)
- Wireless (2)
- XP (13)
- Yahoo (1)
- Youtube (1)
Blog Archive
-
▼
2008
(487)
-
▼
September
(120)
- Rotating pictures in MS Word
- What is Mail Washer? What is Email filtering softw...
- Tutorial on MS Paint
- Print Folder List
- How to Avoid Rapidshare and Megaupload Download Li...
- Top 3 Free Product Key Finder Programs
- Five iPhone tips
- 19 essential get-started tips for Windows Vista
- How to Really reduce the memory usage in Firefox
- How to Double Firefox Speed
- Set your Vista 64 to a faster boot
- Tweak and Customize IE8
- QUICK PREVIEW
- Dealing With Doubles
- Switch Off Use the Web Annoyance
- Error Number: OX80070725 / Description: Incompatib...
- Tutorial to Hide visited websites from others
- How to use calculator in google search engine.
- What is Linux?
- Which Internet Connection plan to choose?
- Internet tips -> What is IP Address? What is DNS?
- Technology tips -> DvD+R vs DVD-R - A comparison
- Email tips -> How to Password protect my email In...
- Email tips -> How to send secret emails by encrypt...
- Hardware Tips -> Problems and Tips while using USB...
- Windows tips -> How to print all files in a folder...
- Windows tips -> Keys for Special Symbols
- George Michael Arrested Over Drug Posession
- LG 60″ Plasma 1080p HDTV
- Xbox 360 price cuts now in effect
- Wink Technology in new gadget makes computer eye-c...
- Britain: 4 Government Laptops Stolen in Another Da...
- Teknocreations InCharge Charges Wiimotes Without O...
- Gadgets At A Glance: MyMiniGolf Crazy Golf
- BlackBerry Bold: Extensively Reviewed
- SanDisk Sansa Fuze Review
- Sony-Ericsson C905 Cyber-shot – 8,1 mega-pixels on...
- AMD introduces ATI Radeon HD 4600 graphics plaque ...
- HDTV market strong, despite economic turmoil
- ASUS is preparing a rival for Omnia with a 5 MP ca...
- Iomega eGo Hard Drive For MacBook Air
- Raon Digital Everun Note Netbook Released
- Elements Stardust Radio
- Sotec E7 All-in-One PC
- Sennheiser VMX Office Bluetooth Headset
- Akshay Kumar to get Rs 71 crore for his next film?
- Nicole Kidman to Star in the 'Eighth Wonder'
- iPhone-Themed Cupcakes Look Yummy
- Congrats On Two Hundred Posting
- New Bluetooth Speakerphone From Sony Ericsson
- Canon Promises 21.1 Megapixels With 5D Mark II
- Leica Pradovit D-1200 Digital Projector
- Logitech Pure-Fi Anytime
- JVC HXD77J Mini System
- Sanyo LP-Z3000 Projector
- Jenga Apartment Tower
- HP TouchSmart IQ816
- mGuard:Theft Recovery Solution for Java Phones
- Spyware Doctor 2008
- Felicity Huffman Thinks Eva Longoria Parker is Fat
- Animated Business Cards
- This “suspension” piano by Seiler is obviously for...
- Make Your Automobile A Portable Kitchen
- LaCie 700 Series Displays
- Vertu Signature S Design
- New iPod touch supports VoIP
- Microsoft develops Vi-Fi (Vehicle Wi-Fi). VoIP whi...
- SanDisk Goes 32GB Flash for Photo/Video Pros
- Make Mine a Mini: Mini-Laptops Driving PC Sales
- Palm TX Handheld
- Create Bad sectors on hard disks
- Volume is too low in my headset while listening to...
- 9 Steps To A Spyware Free Computer
- Disable Welcome Center
- 4G iPod Nano Finally Gives Apple Customers What Th...
- Claudia Mitchell, Bionic Hero
- Asus Eee PC 901 Modded for Mobile Broadband
- Lenovo Offering Sweet Deals on its Laptops
- USB EyeCandy Is for Sticking into Your Mouth
- CHECK VIRUS WHICH MAKE UR CELL RESTARTED.
- In this article I have written some cool tricks in...
- Xp Registry tricks
- Wooden Mobile Phone
- World's Smallest Helicopter Ready For a Spin
- DisplayLink releases OSX driver
- How to clear memory without restarting the unit?
- Rundll.exe Error - What is the best solution for it?
- Kareena's Rs. 6 crore song in Golmaal Returns
- How to Add a Number from Call History to Your Cont...
- MSN Mobile
- Performance Fix For XP Systems Using Radeon Graphi...
- hp pavillion
- Logitech wireless headphones for Ipod
- Victorinox Traveller Lite
- Photoshop Fumbles
- My Maamu is a slave driver: Imran Khan
- How to Unload DLL's to regain memory in Windows XP?
- Chat with your friends through MS-DOS
- How to create a Strong Password?
- How to remove un-used program
-
▼
September
(120)
 RSS Feeds
RSS Feeds





